交叉编译dropbear使能ssh登录以及rt3070wifi模块的移植使用
背景:
之前开发板fl2440与pc的SecureCRT连接的传统方式是用串口转usb线连接,但是之后要用开发板做3G模块的拨号上网等,自己用到无所谓带着usb转串口和开发板就行了,但是要这几个人一块使用这个开发板就成了问题,所以打算用wifi模块连到路由器然后ssh大家都可以连接到开发板进行开发,所以首先需要做的是安装dropbear使能ssh
基本情况:
宿主机系统:CentOS-6.7
嵌入式linux系统:linux 3.0
ssh程序:dropbear
一、交叉编译dropbear使能ssh登录
[wuyujun@wuyujunlocalhost ~]$ cd fl2440/3rdparty/
下载并解压dropbear
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://matt.ucc.asn.au/dropbear/releases/dropbear-2016.74.tar.bz2
[wuyujun@wuyujunlocalhost 3rdparty]$ tar -xjf dropbear-2016.74.tar.bz2
dropbear需要用到zlib库,所以下载并解压zlib
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://github.com/madler/zlib/archive/v1.2.10.tar.gz -O zlib-1.2.10.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ tar -xzf zlib-1.2.10.tar.gz
交叉编译zlib
[wuyujun@wuyujunlocalhost 3rdparty]$ cd zlib-1.2.10
[wuyujun@wuyujunlocalhost zlib-1.2.10]$ ./configure --prefix=`pwd`/../zlib/ --static
[wuyujun@wuyujunlocalhost zlib-1.2.10]$ vim Makefile
修改Makefile内容如下:(配置为对应的交叉编译工具)
CC=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-gcc
LDSHARED=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-gcc
CPP=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-gcc -E
AR=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-ar
保存退出并编译
[wuyujun@wuyujunlocalhost zlib-1.2.10]$ sudo make && make install
[wuyujun@wuyujunlocalhost zlib-1.2.10]$ cd ../zlib/
zlib将会编译安装到fl2440/3rdparty/zlib路径下。
[wuyujun@wuyujunlocalhost zlib]$ ls
include lib share
交叉编译dropbear
进入dropbear解压后的目录
[wuyujun@wuyujunlocalhost zlib]$ cd ..
[wuyujun@wuyujunlocalhost 3rdparty]$ mkdir dropbear
[wuyujun@wuyujunlocalhost 3rdparty]$ cd dropbear-2016.74
[wuyujun@wuyujunlocalhost dropbear-2016.74]$ ./configure --prefix=`pwd`/../dropbear --with-zlib=`pwd`/../zlib/ CC=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-gcc --host=arm
参数--with-zlib=`pwd`/../zlib/ 指定zlib库的位置CC=/opt/xtools/arm920t/bin/arm-arm920t-linux-gnueabi-gcc --host=arm指定交叉编译器
最后交叉编译dropbear
[wuyujun@wuyujunlocalhost dropbear-2016.74]$ make PROGRAMS="dropbear dbclient dropbearkey dropbearconvert scp"
[wuyujun@wuyujunlocalhost dropbear-2016.74]$ make PROGRAMS="dropbear dbclient dropbearkey dropbearconvert scp" install
将dropbear文件夹下的sbin和bin下的所有文件传到开发板的sbin路径下,开发板与主机用网线相连,开发板和主机需要在同一网段能互相通信,开发板使用tftp接收文件
~ >: tftp -gr dropbear 192.168.137.1
dropbear 100% |*******************************| 297k 0:00:00 ETA
~ >: tftp -gr dbclient 192.168.137.1
dbclient 100% |*******************************| 289k 0:00:00 ETA
~ >: tftp -gr dropbearconvert 192.168.137.1
dropbearconvert 100% |*******************************| 146k 0:00:00 ETA
~ >: tftp -gr dropbearkey 192.168.137.1
dropbearkey 100% |*******************************| 137k 0:00:00 ETA
~ >: tftp -gr scp 192.168.137.1
scp 100% |*******************************| 50777 0:00:00 ETA
~ >: mv dbclient dropbear dropbearconvert dropbearkey scp sbin
~ >: cd sbin/
加上执行权限
/sbin >: chmod a+x dbclient dropbear dropbearconvert dropbearkey scp
生成密钥
/sbin >: cd /etc/
/etc >: mkdir dropbear
/etc >: cd dropbear/
/etc/dropbear >: dropbearkey -t rsa -f dropbear_rsa_host_key
/etc/dropbear >: dropbearkey -t dss -f dropbear_dss_host_key
/etc/dropbear >: ls
dropbear_dss_host_key dropbear_rsa_host_key
添加启动脚本
/etc/dropbear >: cd /etc/init.d/
/etc/init.d >: vim S13_dropbear
#!/bin/sh
/sbin/dropbear
保存退出,给脚本加上权限
/etc/init.d >: chmod a+x S13_dropbear
运行dropbear
/etc/init.d >: dropbear
可以看到22号端口被dropbear监听着
/etc/init.d >: netstat -tlnp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 978/dropbear
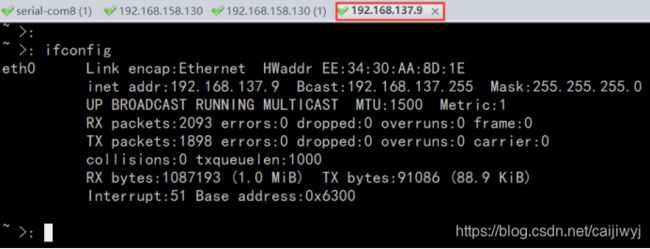
查看ip地址并使用ssh连接到开发板
/etc/init.d >: ifconfig
eth0 Link encap:Ethernet HWaddr EE:34:30:AA:8D:1E
inet addr:192.168.137.9 Bcast:192.168.137.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:2053 errors:0 dropped:0 overruns:0 frame:0
TX packets:1869 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1081898 (1.0 MiB) TX bytes:86278 (84.2 KiB)
Interrupt:51 Base address:0x6300
最后登录成功
参考:https://blog.csdn.net/qq_43260665/article/details/89740503
二、配置Linux内核支持wireless无线上网
1、进入make menuconfig进行配置
[wuyujun@wuyujunlocalhost linux-3.0]$ export TERM=vt100
[wuyujun@wuyujunlocalhost linux-3.0]$ make menuconfig
[*] Networking support --->
-*- Wireless --->
<*> cfg80211 - wireless configuration API
[*] enable powersave by default
[*] enable powersave by default
[*] Wireless extensions sysfs files
[*] cfg80211 wireless extensions compatibility
<*> Common routines for IEEE802.11 drivers
[ ] lib80211 debugging messages (NEW)
<*> Generic IEEE 802.11 Networking Stack (mac80211)
[*] Minstrel
[*] Minstrel 802.11n support
Device Drivers --->
Generic Driver Options --->
(/sbin/hotplug) path to uevent helper
[*] Include in-kernel firmware blobs in kernel binary
[*] Network device support --->
[*] Wireless LAN --->
<*> Ralink driver support --->
--- Ralink driver support
<*> Ralink rt27xx/rt28xx/rt30xx (USB) support
[*] Ralink debug output2、重新编译内核,并烧录到开发板,开机后插入wifi模块,串口打印如下消息
~ >: usb 1-1.1: new full speed USB device number 3 using s3c2410-ohci
phy0 -> rt2x00_set_chip: Info - Chipset detected - rt: 3070, rf: 0005, rev: 0201.
~ >: lsusb
Bus 001 Device 001: ID 1d6b:0001
Bus 001 Device 002: ID 05e3:0606
Bus 001 Device 003: ID 148f:3070
~ >: ifconfig wlan0
wlan0 Link encap:Ethernet HWaddr 00:12:04:24:06:93
BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
第一行:连接类型:Ethernet(以太网)HWaddr(硬件mac地址)
第三行:MULTICAST(支持组播)MTU:1500(最大传输单元):1500字节
第四、五行:接收、发送数据包情况统计
第七行:接收、发送数据字节数统计信息。
三、无线网络配置工具Wireless tools和Wpa_supplicant以及Openssl移植
目前可以使用wireless-tools或wpa_supplicant工具来配置无线网络。但要注意对无线网络的配置是全局性的,而非针对具体的接口。wpa_supplicant是一个较好的选择,但缺点是它不支持所有的驱动。另外,wpa_supplicant目前只能连接到那些你已经配置好ESSID的无线网络。而wireless-tools支持几乎所有的无线网卡和驱动,但它不能连接到那些只支持WPA的AP。
(1)Wireless tools移植
[wuyujun@wuyujunlocalhost ~]$ cd fl2440/3rdparty/
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://hewlettpackard.github.io/wireless-tools/wireless_tools.29.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ tar -xzvf wireless_tools.29.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ mkdir wireless
[wuyujun@wuyujunlocalhost 3rdparty]$ cd wireless_tools.29
[wuyujun@wuyujunlocalhost wireless_tools.29]$ vim Makefile
修改Makefile,主要是修改成相对应的交叉编译器
PREFIX = /home/wuyujun/fl2440/3rdparty/wireless
#因为交叉编译仅是给fl2440开发板用的不需要安装到/usr/local路径下面,安装到刚创建的目录下面
## Compiler to use (modify this for cross compile).
CC = /opt/xtools/arm920t/bin/arm-linux-gcc
## Other tools you need to modify for cross compile (static lib only).
AR = /opt/xtools/arm920t/bin/arm-linux-ar
RANLIB = /opt/xtools/arm920t/bin/arm-linux-ranlib
[wuyujun@wuyujunlocalhost wireless_tools.29]$ make
[wuyujun@wuyujunlocalhost wireless_tools.29]$ make install
在该目录下找到libiw.so.29,下载到开发板的/lib/目录下;再该目录下找到iwpriv、iwconfig、iwlist, iwevent, iwspy等这些绿色可执行的文件,下载到开发板的/bin目录下。这时就应该可以使用这些命令通过网卡搜索到环境中的无线网络。
~ >: tftp -gr libiw.so.29 192.168.137.1
~ >: chmod a+x libiw.so.29
~ >: mv libiw.so.29 /lib
其他的也传到开发板下
~ >: chmod a+x iw*
~ >: chmod a+x ifrename
~ >: mv iw* /bin
~ >: mv ifrename /bin
使用一个命令试试是否成功
~ >: iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0 IEEE 802.11bgn ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=0 dBm
Retry long limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:on
(2)Openssl工具移植
现在的wifi网络大多都是WPA加密,所以wpa_supplicant对我们来说除了配置无线网络的需求之外,它更主要是用来支持WEP,WPA/WPA2和WAPI无线协议和加密认证的。而要加密就要使用到相关的加密算法,常用的密钥等,所以我们要先移植Openssl工具再移植wpa-supplicant。因为后面编译wpa_supplicant要依赖openssl中的lib和include
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://coding.net/u/sfantree/p/self_use_OSS/git/raw/master/source/openssl-1.0.0s.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ tar -xzf openssl-1.0.0s.tar.gz
创建安装路径
[wuyujun@wuyujunlocalhost openssl-1.0.0s]$ mkdir install
修改Makefile
[wuyujun@wuyujunlocalhost openssl-1.0.0s]$ vim Makefile
INSTALLTOP=/home/wuyujun/fl2440/3rdparty/openssl-1.0.0s/install
OPENSSLDIR=/home/wuyujun/fl2440/3rdparty/openssl-1.0.0s/install
CC= /opt/xtools/arm920t/bin/arm-linux-gcc
AR= /opt/xtools/arm920t/bin/arm-linux-ar $(ARFLAGS) r
RANLIB= /opt/xtools/arm920t/bin/arm-linux-ranlib
[wuyujun@wuyujunlocalhost openssl-1.0.0s]$ make&&make install
[wuyujun@wuyujunlocalhost openssl-1.0.0s]$ ls install/lib/
engines libcrypto.a libssl.a pkgconfig
把 libcrypto.a libssl.a放到开发板/lib下
(3)wpa_supplicant驱动移植
wpa_supplicant本是开源项目源码,被谷歌修改后加入Android移动平台,它主要是用来支持WEP,WPA/WPA2和WAPI无线协议和加密认证的,而实际上的工作内容是通过socket(不管是wpa_supplicant与上层还是wpa_supplicant与驱动都采用socket通讯)与驱动交互上报数据给用户,而用户可以通过socket发送命令给wpa_supplicant调动驱动来对WiFi芯片操作。 简单的说,wpa_supplicant就是WiFi驱动和用户的中转站外加对协议和加密认证的支持。
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://coding.net/u/sfantree/p/self_use_OSS/git/raw/master/source/wpa_supplicant-0.7.3.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ tar -xzvf wpa_supplicant-0.7.3.tar.gz
[wuyujun@wuyujunlocalhost 3rdparty]$ cd wpa_supplicant-0.7.3
[wuyujun@wuyujunlocalhost wpa_supplicant-0.7.3]$ cd wpa_supplicant/
[wuyujun@wuyujunlocalhost wpa_supplicant]$ cp defconfig .config
[wuyujun@wuyujunlocalhost wpa_supplicant]$ vim .config
#### sveasoft (e.g., for Linksys WRT54G) ######################################
#CC=mipsel-uclibc-gcc
CC=/opt/xtools/arm920t/bin/arm-linux-gcc -L /home/wuyujun/fl2440/3rdparty/openssl-1.0.0s/install/lib
#CFLAGS += -Os
CFLAGS +=-I /home/wuyujun/fl2440/3rdparty/openssl-1.0.0s/install/include
#CPPFLAGS += -I../src/include -I../../src/router/openssl/include
LIBS +=-L /home/wuyujun/fl2440/3rdparty/openssl-1.0.0s/install/lib
#LIBS += -L/opt/brcm/hndtools-mipsel-uclibc-0.9.19/lib -lssl
###############################################################################
编译
[wuyujun@wuyujunlocalhost wpa_supplicant]$ make
然后将wpa_cli,wpa_supplicant,wpa_passphrase传到开发板的/bin目录下,并加上执行权限
四、使能rt3070无线网卡
下载3070固件,放到开发板/lib/firmware下,通常情况下,load firmware的动作是通过用户空间的hotplug handler,也就是/proc/sys/kernel/hotplug里设定的执行档,来完成。root_qtopia默认会在/etc/init.d/rcS里将/proc/sys/kernel/hotplug设定为/sbin/mdev,即busybox的mdev模块。它在收到来自内核的请求加载rt3070.bin这个firmware消息后,会从/lib/firmware目录下去找rt3070.bin,如果能找到就加载
下载rt2870.bin
[wuyujun@wuyujunlocalhost 3rdparty]$ wget https://coding.net/u/sfantree/p/self_use_OSS/git/raw/master/source/rt2870.bin
传到开发板上
~ >: tftp -gr rt2870.bin 192.168.137.1
/lib/fireware >: mv ~/rt2870.bin rt2870.bin
/lib/fireware >: ls
rt2870.bin
要给它加上权限,否则会报错Error - Failed to request Firmware.
/lib/firmware >: chmod a+x rt2870.bin
~ >: ifconfig wlan0 up
phy1 -> rt2x00lib_request_firmware: Info - Loading firmware file 'rt2870.bin'.
phy1 -> rt2x00lib_request_firmware: Info - Firmware detected - version: 0.29.
phy1 -> rt2x00mac_conf_tx: Info - Configured TX queue 0 - CWmin: 3, CWmax: 4, Aifs: 2, TXop: 102.
phy1 -> rt2x00mac_conf_tx: Info - Configured TX queue 1 - CWmin: 4, CWmax: 5, Aifs: 2, TXop: 188.
phy1 -> rt2x00mac_conf_tx: Info - Configured TX queue 2 - CWmin: 5, CWmax: 10, Aifs: 3, TXop: 0.
phy1 -> rt2x00mac_conf_tx: Info - Configured TX queue 3 - CWmin: 5, CWmax: 10, Aifs: 7, TXop: 0.
使能成功
五、rt3070无线模块连接路由器
/lib/firmware >: cd
~ >: cd apps/
/apps >: mkdir etc
/apps >: cd etc/
/apps/etc >: mkdir wireless
/apps/etc >: cd wireless
在开发板上输入命令:wpa_passphrase ssid psk>>wpa_supplicant.conf(ssid就是你wifi的名字 psk就是密码)
/apps/etc/wireless >: wpa_passphrase LingYun_XiaoMi lingyun_emb >> wpa_supplicant.conf
/apps/etc/wireless >: ls
wpa_supplicant.conf
/apps/etc/wireless >: cat wpa_supplicant.conf
network={
ssid="LingYun_XiaoMi"
#psk="lingyun_emb"
psk=136a6b18bd0d21eb12d6bc591fa652d628cbb438e8f29fcfeb8d763c0bf15ec2
}
修改配置文件如下:
/apps/etc/wireless >: vim wpa_supplicant.conf
# WPA-PSK/TKIP
# wpa_supplicant -Dwext -iwlan0 -c/apps/etc/wireless/wpa_supplicant.conf
ctrl_interface=/var/run/wpa_supplicant
network={
ssid="LingYun_XiaoMi"
key_mgmt=WPA-PSK
proto=WPA2
pairwise=TKIP CCMP
group=TKIP CCMP
#psk="lingyun_emb"
psk=136a6b18bd0d21eb12d6bc591fa652d628cbb438e8f29fcfeb8d763c0bf15ec2
}
激活网卡
/apps/etc/wireless >: ifconfig wlan0 up
~ >: wpa_supplicant -Dwext -iwlan0 -c/apps/etc/wireless/wpa_supplicant.conf &
Trying to associate with 50:64:2b:31:11:9a (SSID='LingYun_XiaoMi' freq=2422 MHz)
phy0 -> rt2x00mac_conf_tx: Info - Configured TX queue 2 - CWmin: 4, CWmax: 10, Aifs: 3, TXop: 0.
phy0 -> rt2x00mac_conf_tx: Info - Configured TX queue 3 - CWmin: 4, CWmax: 10, Aifs: 7, TXop: 0.
phy0 -> rt2x00mac_conf_tx: Info - Configured TX queue 1 - CWmin: 3, CWmax: 4, Aifs: 2, TXop: 94.
phy0 -> rt2x00mac_conf_tx: Info - Configured TX queue 0 - CWmin: 2, CWmax: 3, Aifs: 2, TXop: 47.
Associated with 50:64:2b:31:11:9a
WPA: Key negotiation completed with 50:64:2b:31:11:9a [PTK=CCMP GTK=TKIP]
CTRL-EVENT-CONNECTED - Connection to 50:64:2b:31:11:9a completed (auth) [id=0 id_str=]
~ >: iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0 IEEE 802.11bgn ESSID:"LingYun_XiaoMi"
Mode:Managed Frequency:2.422 GHz Access Point: 50:64:2B:31:11:9A
Bit Rate=6.5 Mb/s Tx-Power=20 dBm
Retry long limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:on
Link Quality=61/70 Signal level=-49 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:0 Missed beacon:0
~ >: ifconfig
eth0 Link encap:Ethernet HWaddr BA:25:AF:C3:89:FB
inet addr:192.168.137.9 Bcast:192.168.137.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:143 errors:0 dropped:0 overruns:0 frame:0
TX packets:32 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:19609 (19.1 KiB) TX bytes:5694 (5.5 KiB)
Interrupt:51 Base address:0x6300
wlan0 Link encap:Ethernet HWaddr 00:12:04:23:B0:89
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:776 errors:0 dropped:0 overruns:0 frame:0
TX packets:2 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:34552 (33.7 KiB) TX bytes:288 (288.0 B)
网络设置:
未开启DHCP,所以得手动分配:
设置IP
~ >: ifconfig wlan0 192.168.0.198
设置默认网关
~ >: route add default gw 192.168.0.1
设置DNS
~ >: echo "nameserver 8.8.8.8" > /etc/resolv.conf
用ping命令测试网络
~ >: ping baidu.com
PING baidu.com (220.181.38.148): 56 data bytes
64 bytes from 220.181.38.148: seq=0 ttl=53 time=25.000 ms
64 bytes from 220.181.38.148: seq=1 ttl=53 time=70.000 ms
64 bytes from 220.181.38.148: seq=7 ttl=53 time=65.000 ms
64 bytes from 220.181.38.148: seq=8 ttl=53 time=65.000 ms
^C
--- baidu.com ping statistics ---
开启DHCP:
busybox已经集成了DHCP的客户端和服务端,make编译后,我们只要把Busybox的examples/udhcp/simple.script 拷贝到开发板/usr/share/udhcpc/下,并重命名为default.script,然后更改文件default.script的权限。
[wuyujun@wuyujunlocalhost ~]$ cd fl2440/3rdparty/busybox-1.27.1/examples/udhcp/
[wuyujun@wuyujunlocalhost udhcp]$ ls
sample.bound sample.deconfig sample.nak sample.renew sample.script simple.script udhcpd.conf
~ >: mv simple.script default.script
~ >: chmod a+x default.script
~ >: cd /usr/
/usr >: mkdir -p share/udhcpc/
/usr >: cd share/udhcpc/
/usr/share/udhcpc >: mv /default.script default.script
/usr/share/udhcpc >: ls
default.script
/usr/share/udhcpc >: udhcpc -i wlan0
udhcpc: started, v1.27.1
Setting IP address 0.0.0.0 on wlan0
udhcpc: sending discover
udhcpc: sending select for 192.168.0.105
udhcpc: lease of 192.168.0.105 obtained, lease time 43200
Setting IP address 192.168.0.105 on wlan0
Deleting routers
route: SIOCDELRT: No such process
Adding router 192.168.0.1
Recreating /etc/resolv.conf
Adding DNS server 192.168.0.1
动态获取ip地址成功
/usr/share/udhcpc >: ifconfig
eth0 Link encap:Ethernet HWaddr BA:25:AF:C3:89:FB
inet addr:192.168.137.9 Bcast:192.168.137.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:78 errors:0 dropped:0 overruns:0 frame:0
TX packets:41 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:16532 (16.1 KiB) TX bytes:4412 (4.3 KiB)
Interrupt:51 Base address:0x6300
wlan0 Link encap:Ethernet HWaddr 00:12:04:23:B0:89
inet addr:192.168.0.105 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4118 errors:0 dropped:253 overruns:0 frame:0
TX packets:13 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:195554 (190.9 KiB) TX bytes:3970 (3.8 KiB)
/usr/share/udhcpc >: ping baidu.com
PING baidu.com (220.181.38.148): 56 data bytes
64 bytes from 220.181.38.148: seq=0 ttl=53 time=25.000 ms
64 bytes from 220.181.38.148: seq=1 ttl=53 time=75.000 ms
64 bytes from 220.181.38.148: seq=2 ttl=53 time=65.000 ms
64 bytes from 220.181.38.148: seq=3 ttl=53 time=65.000 ms
^C
--- baidu.com ping statistics ---
最后在同一个局域网内,就可以通过ssh远程连接到开发板上进行开发了
下面是有关wifi无线网络的相关知识,转载至:https://blog.csdn.net/baweiyaoji/article/details/72229183
1、计算机网络->无线网络的几种常见标准:
IEEE802.11a:使用5GHz频段,传输速度54Mbps,与802.11b不兼容;
IEEE 802.11b:使用2.4GHz频段,传输速度11Mbps;
IEEE802.11g:使用2.4GHz频段,传输速度主要有54Mbps、108Mbps,可向下兼容802.11b;
IEEE802.11n草案:使用2.4GHz频段,传输速度可达300Mbps,标准尚为草案,但产品已层出不穷;
目前IEEE802.11b最常用,但IEEE802.11g更具下一代标准的实力,802.11n也在快速发展中。
IEEE 802.11是如今无线局域网通用的标准。
2、WiFi无线网络的几种认证与加密方式:
Open System:完全不认证也不加密,任何人都可以连到无线基地台使用网络。
WEP (Wired Equivalent Privacy) 有线等效加密:最基本的加密技术,手机用户、笔记型计算机与无线网络的Access Point拥有相同的网络密钥,才能解读互相传递的数据。密钥分为64bits及128bits两种,最多可设定四组不同的密钥。当用户端进入WLAN前必须输入正确的密钥才能进行连接。
WPA (Wi-Fi Protected Access) 商务宝采用的加密方式:由Wi-Fi Alliance (http://www.wi-fi.com/)所提出的无线安全标准,有分成家用的WPA-PSK (Pre-Shared Key)与企业用的WPA-Enterprise版本。
WPA2:WPA的加强版,也就是IEEE 802.11i无线网络标准。同样有家用的PSK版本与企业的IEEE 802.1x版本。WPA2与WPA的差别在于,它使用更安全的加密技术AES (Advanced Encryption Standard),因此比WPA更难被破解、更安全。
MAC ACL (Access Control List):MAC ACL只能用于认证而不能用于加密。在无线基地台输入允许被连入的无线网卡MAC地址,不在此清单的无线网卡无法连入无线基地台。
RT3070有两种工作模式:STA(station)模式和SoftAP(Access Point)模式。STA即客户端模式,即利用rt3070连接路由器进行上网。有了wifi模块和3G模块也可以用开发板来做个路由器提供wifi,这样就是SoftAP模式
参考:https://blog.csdn.net/fml1997/article/details/72803222
https://blog.csdn.net/baweiyaoji/article/details/72229183