tee-pwn-00-HITCON 2018-Super Hexagon-biso.bin包含的内容
准备-IDA插件
https://github.com/gdelugre/ida-arm-system-highlight
https://github.com/NeatMonster/AMIE
通过binwalk,hexdump,010-editor大概分析
binwalk观察
$ binwalk bios.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
143472 0x23070 SHA256 hash constants, little endian
770064 0xBC010 ELF, 64-bit LSB executable, version 1 (SYSV)
792178 0xC1672 Unix path: /lib/libc/aarch64
792711 0xC1887 Unix path: /lib/libc/aarch64
794111 0xC1DFF Unix path: /lib/libc/aarch64
796256 0xC2660 Unix path: /home/seanwu/hitcon-ctf-2018
只看到存在一个elf文件
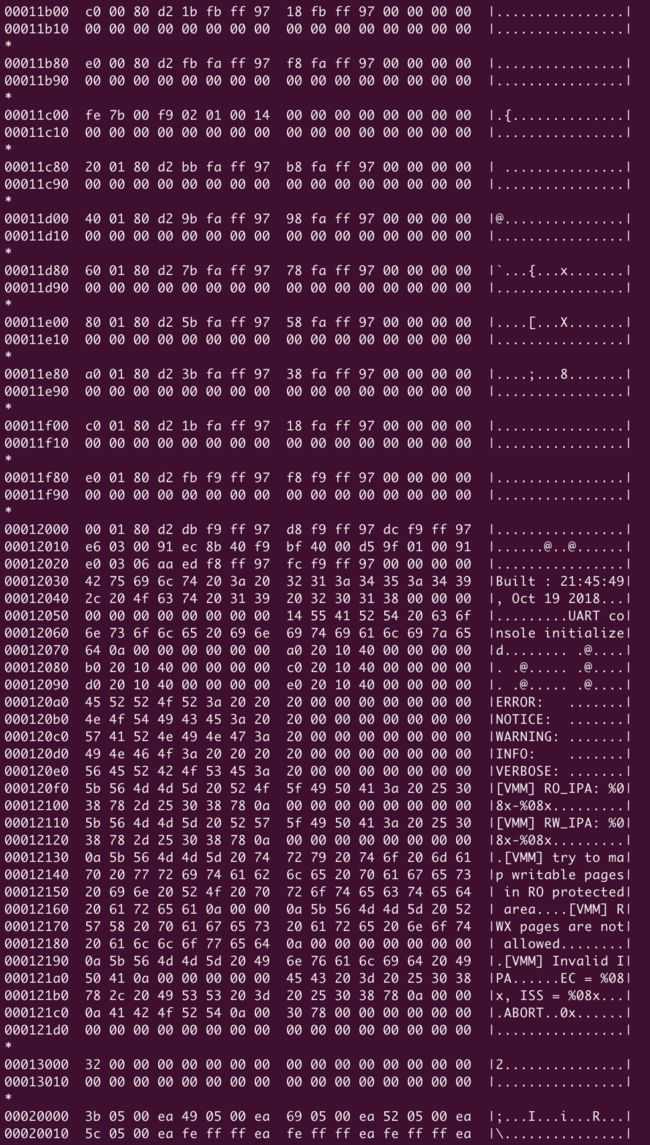
hexdump观察-可以看到明显的分隔(这里需要了解异常向量表)
00000000 ~ 000028b0 | 00010000
00010000 ~ 00013010 | 0x20000
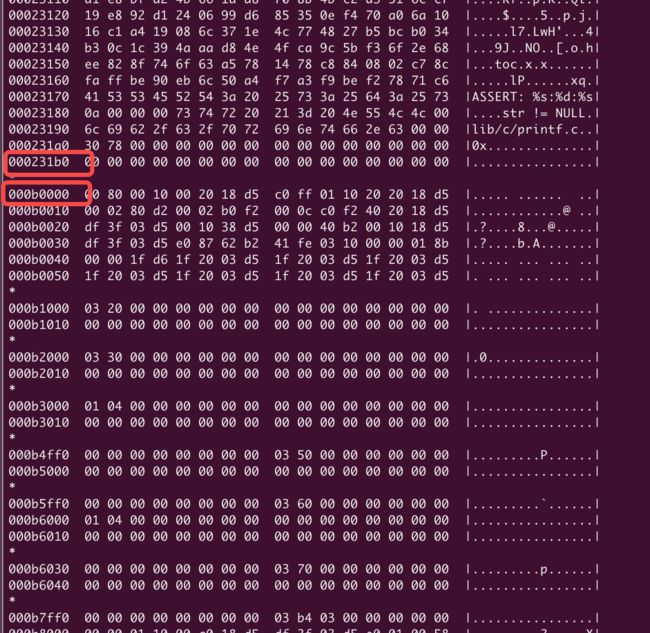
00020000 ~ 000231b0 | 000b0000
000b0000 ~ 000baa00 | 000bc000
000bc000 ~ 000c8bd8
通过hexdump可以很直观的看到bios.bin 由5个部分链接组成,其中0x80大小的碎块是中断处理函数
- 00000000 ~ 000028b0 | 00010000
- 00010000 ~ 00013010 | 0x20000
- 00020000 ~ 000231b0 | 000b0000
- 000b0000 ~ 000baa00 | 000bc000
- 000bc000 ~ 000c8bd8
提取内容,分析架构
先通过dd将这些明显分段的内容提取出来
dd if=bios.bin of=00000000_000028b0_00010000.bin bs=1 skip=0 count=0x28b0
dd if=bios.bin of=00010000_00013010_00020000.bin bs=1 skip=0x10000 count=0x3010
dd if=bios.bin of=00020000_000231b0_000b0000.bin bs=1 skip=0x20000 count=0x31b0
dd if=bios.bin of=000b0000_000baa00_000bc000.bin bs=1 skip=0xb0000 count=0xaa00
dd if=bios.bin of=000bc000_000c8bd8_end.bin bs=1 skip=0xbc000 count=0xCBD8
分析架构
binwalk -A 00000000_000028b0_00010000.bin - aarch64
binwalk -A 00010000_00013010_00020000.bin - aarch64
binwalk -A 00020000_000231b0_000b0000.bin 没分析出来架构
binwalk -A 000b0000_000baa00_000bc000.bin - aarch64
binwalk -A 000bc000_000c8bd8_end.bin - aarch64
这里00020000_000231b0_000b0000.bin没有出来,通过ida分别指定架构arm,armv8,看起来不是字符串的就用c进行识别,可以分析出00020000_000231b0_000b0000.bin属于arm架构
binwalk -A 00000000_000028b0_00010000.bin - aarch64
binwalk -A 00010000_00013010_00020000.bin - aarch64
binwalk -A 00020000_000231b0_000b0000.bin - arm
binwalk -A 000b0000_000baa00_000bc000.bin - aarch64
binwalk -A 000bc000_000c8bd8_end.bin - aarch64
分析各文件所属EL级别
00000000_000028b0_00010000_aarch64.bin
通过binwalk分析各段的内容,啥都没分析出来
╰─○ binwalk 00000000_000028b0_00010000_aarch64.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
放到IDA64-armv8里面试试,不像字符串的就按c识别试试

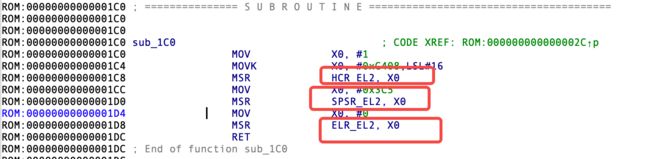
识别出来,能处理EL3,大概就是EL3相关的处理程序了
00010000_00013010_00020000_aarch64.bin
binwalk 看下来也是什么都没有
╰─○ binwalk 00010000_00013010_00020000_aarch64.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
猜测属于EL2
000b0000_000baa00_000bc000_aarch64.bin
╰─○ binwalk 000b0000_000baa00_000bc000_aarch64.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
放入IDA64-arm小端-aarch64啥都没分析出来
尝试IDA64-arm大端-aarch64,有内容了(amie插件识别不了大端的系统寄存器)
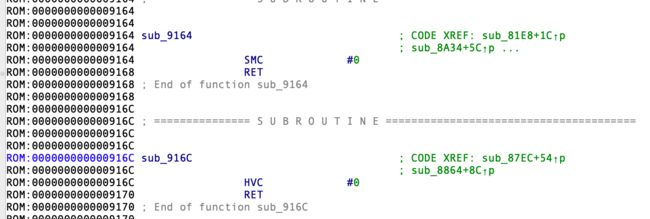
发现有调用EL3,EL2的指令,但是插件出了些问题
https://github.com/gdelugre/ida-arm-system-highlight
https://github.com/NeatMonster/AMIE
换ghidra,aarch64-big end - default

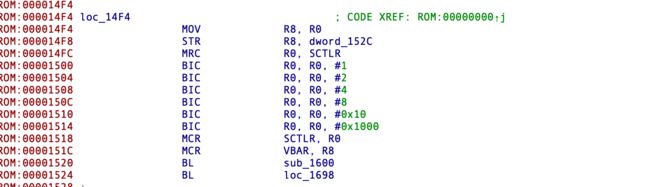
操作了TTBR0_EL1,TTBR1_EL1,这个应该是EL1的kernel了
00020000_000231b0_000b0000_arch.bin
有点内容,但是不知道是啥
╰─○ binwalk 00020000_000231b0_000b0000_arch.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
12400 0x3070 SHA256 hash constants, little endian
该程序段可存在特权,猜测是S-EL1
000bc000_000c8bd8_end_aarch64.bin
╰─○ binwalk 000bc000_000c8bd8_end_aarch64.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
16 0x10 ELF, 64-bit LSB executable, version 1 (SYSV)
22130 0x5672 Unix path: /lib/libc/aarch64
22663 0x5887 Unix path: /lib/libc/aarch64
24063 0x5DFF Unix path: /lib/libc/aarch64
26208 0x6660 Unix path: /home/seanwu/hitcon-ctf-2018
╰─○ dd if=000bc000_000c8bd8_end_aarch64.bin of=000bc010_000c8bd8_end_aarch64.elf bs=1 skip=0x10
52168+0 records in
52168+0 records out
52168 bytes transferred in 0.203992 secs (255736 bytes/sec)
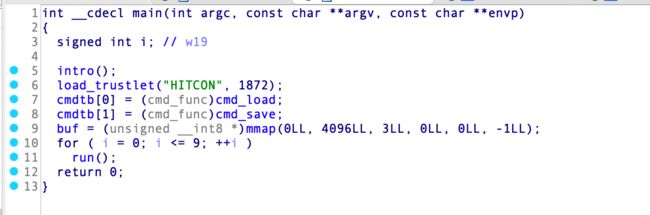
看起来像是一个EL0的程序
汇总
EL0_000bc010_000c8bd8_end_aarch64.elf
EL1_000b0000_000baa00_000bc000_aarch64.bin
EL2_00010000_00013010_00020000_aarch64.bin
EL3_00000000_000028b0_00010000_aarch64.bin
S-EL1_00020000_000231b0_000b0000_arch.bin
好像还少一个S-EL0,之后再分析