ncstisc-2018-babydriver:UAF
启动脚本
#! /bin/sh
qemu-system-x86_64 \
-initrd rootfs.cpio \
-kernel bzImage \
-append 'console=ttyS0 root=/dev/ram oops=panic panic=1' /dev/null \
-m 64M --nographic \
-smp cores=1,threads=1 -cpu kvm64,+smep
只可开启了smep保护
题目信息
babyopen
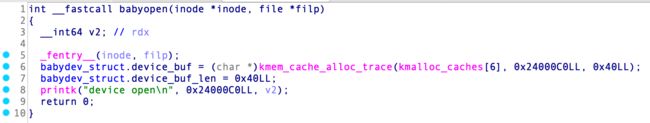
每次open(驱动名称),都会为babydev_struct.device_buf全局变量分配0x40大小的堆空间
babyrelease

关闭close(驱动文件描述符),会通过kfree()释放掉申请的堆空间,但是这里有个问题,没有将babydev_struct.device_buf置NULL
这里便存在一个问题,当连续两次打开驱动时,fd1,fd2 babydev_struct.device_buf 指向的是同一个堆空间
int fd1 = open("/dev/babydev", O_RDWR);
int fd2 = open("/dev/babydev", O_RDWR);
当close(fd1),由于没将babydev_struct.device_buf置NULL,导致fd2可以继续读写babydev_struct.device_buf指向的堆空间,UAF形成
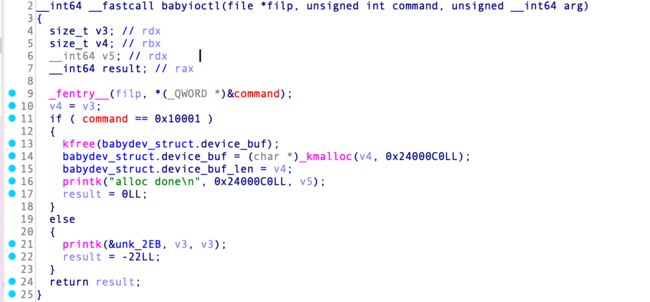
babyioctl
这里,可能题目还是怕选手觉得难,可以让选手创建任意大小的UAF
利用方式
下面两种都用方式大致相同
- 通过babyopen,babyopen让两个文件描述符fd1,fd2指向同一个
babydev_struct.device_buf - babyioctl,
command==0x10001,调整babydev_struct.device_buf指向的堆为自己期望的大小 - close(fd1); (
babydev_struct.device_buf指向的堆被kfree) - 用户层调用,使产生合适的堆结构占据被释放掉的堆
- 读这个堆结构,可以获取其中包含的内核函数地址,经过简单计算可以获取内核基地址
- 写这个堆结构,覆写里面的函数指针
保存的地址,使得在用户态操作时,可以触发函数指针执行 - 由于存在
smep保护,一般被覆写里面的函数指针为一个栈迁移rop,然后在用户态布置rop提权
UAF seq_operations
#define _GNU_SOURCE
#include UAF tty_operations
#include