华为MPLSVPN与GRE隧道配置练习
华为MPLS-VPN配置练习
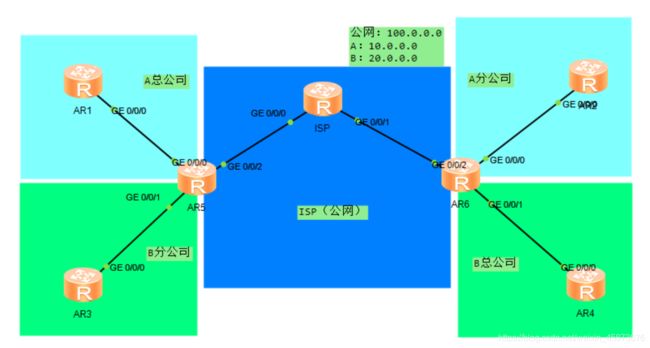
- 一、拓扑以及需求
- 二、配置思路
-
- (1)模拟运营商ISP网络
-
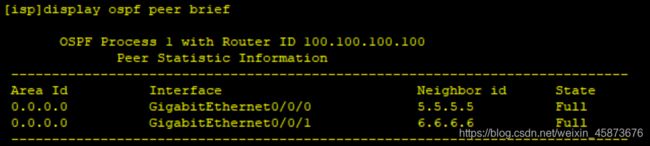
- 1、底层OSPF1
- 2、R5-R6起BGP邻居
- 3、全网段配置MPLS
- (2)A公司配置MPLS-VPN
-
- 1、起VRF空间
- 2、在VRF空间中起协议
- 3、测试连通性
- 4、路由引入
- 5、测试连通性
- (3)B公司配置隧道
-
- 1、配置GRE隧道
- 2、起协议
- 3、连通性测试
- (4)两种技术对比
- 三、本拓扑所有路由器的完整配置
-
- R5
- R6
- ISP
- R1
- R2
- R3
- R4
一、拓扑以及需求
因业务需求,AB两公司需要开设分公司,拉专线太贵,做个VPN吧,两公司最后决定:
A公司做MPLS-VPN;B公司做隧道。
二、配置思路
(1)模拟运营商ISP网络
1、底层OSPF1
这里以ISP配置为例,具体配置如下:
ISP配置如下:
[isp]ospf 1 router-id 100.100.100.100
[isp-ospf-1]area 0
[isp-ospf-1-area-0.0.0.0]network 100.100.100.100 0.0.0.0
[isp-ospf-1-area-0.0.0.0]network 100.200.50.1 0.0.0.0
[isp-ospf-1-area-0.0.0.0]network 100.200.60.1 0.0.0.0
2、R5-R6起BGP邻居
这里以R5配置为例,具体配置如下:
R5具体配置如下:
[r5]bgp 1
[r5-bgp]peer 6.6.6.6 as-number 1
[r5-bgp]peer 6.6.6.6 connect-interface LoopBack 0
[r5-bgp]peer 6.6.6.6 next-hop-local
# 开启VPNV4路由
[r5-bgp]ipv4-family v4
[r5-bgp-af-v4]peer 6.6.6.6 enable
3、全网段配置MPLS
这里以R5配置为例,具体配置如下:
R5的MPLS-LDP(LSP隧道)开启配置如下:
#全局开启:
[isp]mpls lsr-id 5.5.5.5
[isp]mpls
Info: Mpls starting, please wait... OK!
[isp-mpls]mpls ldp
[r5-mpls-ldp]q
#接口开启
[isp]interface GigabitEthernet 0/0/0
[isp-GigabitEthernet0/0/0]mpls
[isp-GigabitEthernet0/0/0]mpls ldp
[isp]interface GigabitEthernet 0/0/1
[isp-GigabitEthernet0/0/1]mpls
[isp-GigabitEthernet0/0/1]mpls ldp
(2)A公司配置MPLS-VPN
这里以R5配置为例,具体配置如下:
1、起VRF空间
R5的MPLS-VPN配置如下:
#创建VRF空间:名称为a1
#RD(route-distinguisher):1:1
#RT(-targe):1:1
[r5]ip -instance a1
[r5--instance-a1]route-distinguisher 1:1
[r5--instance-a1-af-ipv4]-target 1:1
IVT Assignment result:
Info: VPN-Target assignment is successful.
EVT Assignment result:
Info: VPN-Target assignment is successful.
[r5--instance-a1-af-ipv4]quit
[r5--instance-a1]quit
#接口绑定VRF空间,通俗可理解为将此接口关在小黑屋内
#注意:需要先绑定后配置IP地址,先关后配!
[r5]interface GigabitEthernet 0/0/0
[r5-GigabitEthernet0/0/0]ip binding -instance a1
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[r5-GigabitEthernet0/0/0]ip address 10.200.15.2 24
2、在VRF空间中起协议
在VRF空间中起不同进程的OSPF协议,以R5为例:
R5起OSPF2具体配置:
[r5]ospf 2 router-id 5.5.5.5 -instance a1
[r5-ospf-2]area 0
[r5-ospf-2-area-0.0.0.0]network 10.200.15.2 0.0.0.0
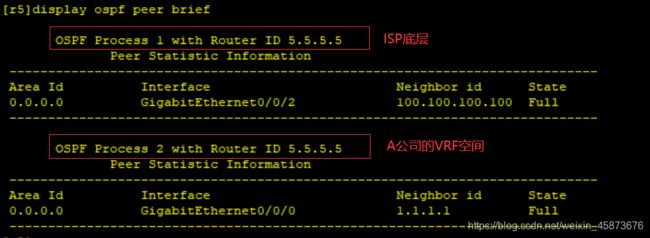
3、测试连通性
R1-R5:
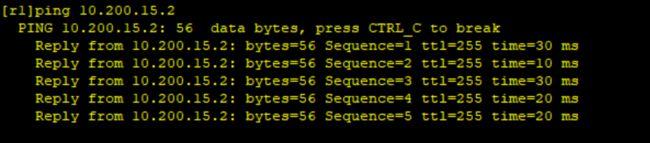
R5-R1:
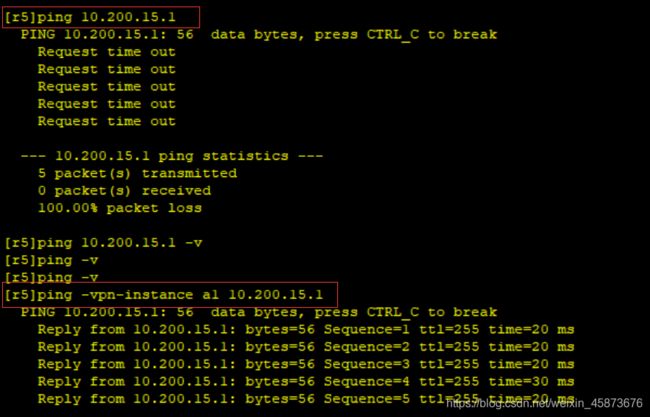
R5pingR1不通原因: 由于VRF空间的存在,R5中现在存在两张路由表,一张为公共路由表另一张为VRF空间的路由表,在普通ping的情况下会默认查公共路由表,不会查VRF表,所以不通。
通俗来讲:公共路由表就好比一个别墅,将某一接口关进小黑屋以后它就不在别墅中了,找东西会默认在别墅中找,因此想找小黑屋中的东西时因指明小黑屋咋走,例如:“--instance a1”。
4、路由引入
在BGP和OSPF中做双向重发布,配置如下:
# BGP在ipv4-family重发布
[r5]bgp 1
[r5-bgp]ipv4-family -instance a1
[r5-bgp-a1]import-route ospf 2
# OSPF重发布
[r5]ospf 2
[r5-ospf-2]import-route bgp
5、测试连通性
(3)B公司配置隧道
1、配置GRE隧道
以R6为例,配置如下:
# GRE隧道
[r6]interface Tunnel 0/0/0
[r6-Tunnel0/0/0]ip address 20.200.56.2 24
[r6-Tunnel0/0/0]tunnel-protocol gre
[r6-Tunnel0/0/0]source 100.200.60.2
[r6-Tunnel0/0/0]destination 10.200.50.2
[r5]interface Tunnel 0/0/0
[r5-Tunnel0/0/0]ip address 20.200.56.1 24
[r5-Tunnel0/0/0]tunnel-protocol gre
[r5-Tunnel0/0/0]source 100.200.50.2
[r5-Tunnel0/0/0]destination 10.200.60.2
2、起协议
这里我们选择起RIP协议,配置以R3为例:
# R3的RIP协议配置:
[r3]rip 2
[r3-rip-2]version 2
[r3-rip-2]undo summary
[r3-rip-2]network 3.0.0.0
[r3-rip-2]network 20.0.0.0
注:在OSPF协议中宣告路由时:需要宣告物理接口的路由!!!不是Tunnel口的路由!!
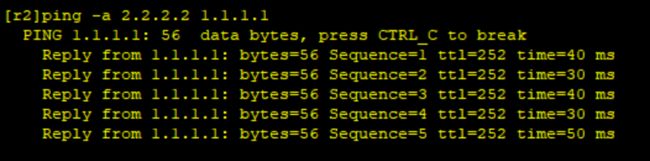
3、连通性测试
(4)两种技术对比
首先无论是MPLS-VPN还是GRE隧道技术,均可以达到连通异地私网的目的。
不同在于,MPLS-VPN是利用标签,它是存在于2.5层的技术,在设备的需求上它需要公网区域经过的所有路由器均支持MPLS,对设备要求较高。
GRE隧道技术是位于3层的技术,它是在逻辑上将异地私网连在一起,在设备需求上仅需要边界连接的设备支持MPLS即可,相比之下对设备要求较低。
三、本拓扑所有路由器的完整配置
R5
[r5]display current-configuration
[V200R003C00]
#
sysname r5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
ip -instance a1
ipv4-family
route-distinguisher 1:1
-target 1:1 export-extcommunity
-target 1:1 import-extcommunity
#
mpls lsr-id 5.5.5.5
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip binding -instance a1
ip address 10.200.15.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 20.200.35.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 100.200.50.2 255.255.255.0
mpls
mpls ldp
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
interface Tunnel0/0/0
ip address 20.200.56.1 255.255.255.0
tunnel-protocol gre
source 100.200.50.2
destination 100.200.60.2
#
bgp 1
peer 6.6.6.6 as-number 1
peer 6.6.6.6 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 6.6.6.6 enable
peer 6.6.6.6 next-hop-local
#
ipv4-family v4
policy -target
peer 6.6.6.6 enable
#
ipv4-family -instance a1
import-route ospf 2
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 5.5.5.5 0.0.0.0
network 100.200.50.2 0.0.0.0
#
ospf 2 router-id 5.5.5.5 -instance a1
import-route bgp
area 0.0.0.0
network 10.200.15.2 0.0.0.0
#
rip 2
undo summary
version 2
network 20.0.0.0
network 100.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R6
[r6]display current-configuration
[V200R003C00]
#
sysname r6
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
ip -instance a1
ipv4-family
route-distinguisher 1:1
-target 1:1 export-extcommunity
-target 1:1 import-extcommunity
#
mpls lsr-id 6.6.6.6
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip binding -instance a1
ip address 10.200.26.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 20.200.46.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 100.200.60.2 255.255.255.0
mpls
mpls ldp
#
interface NULL0
#
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
#
interface Tunnel0/0/0
ip address 20.200.56.2 255.255.255.0
tunnel-protocol gre
source 100.200.60.2
destination 100.200.50.2
#
bgp 1
peer 5.5.5.5 as-number 1
peer 5.5.5.5 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 5.5.5.5 enable
peer 5.5.5.5 next-hop-local
#
ipv4-family v4
policy -target
peer 5.5.5.5 enable
#
ipv4-family -instance a1
import-route ospf 2
#
ospf 1 router-id 6.6.6.6
area 0.0.0.0
network 6.6.6.6 0.0.0.0
network 100.200.60.2 0.0.0.0
#
ospf 2 router-id 6.6.6.6 -instance a1
import-route bgp
area 0.0.0.0
network 10.200.26.2 0.0.0.0
#
rip 2
undo summary
version 2
network 20.0.0.0
network 100.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
ISP
[isp]display current-configuration
[V200R003C00]
#
sysname isp
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
mpls lsr-id 100.100.100.100
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 100.200.50.1 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
ip address 100.200.60.1 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 100.100.100.100 255.255.255.255
#
ospf 1 router-id 100.100.100.100
area 0.0.0.0
network 100.100.100.100 0.0.0.0
network 100.200.50.1 0.0.0.0
network 100.200.60.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R1
[r1]display current-configuration
[V200R003C00]
#
sysname r1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.200.15.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ospf 2 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.200.15.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R2
[r2]display current-configuration
[V200R003C00]
#
sysname r2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.200.26.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
ospf 2 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 10.200.26.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R3
[r3]display current-configuration
[V200R003C00]
#
sysname r3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 20.200.35.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
rip 2
undo summary
version 2
network 3.0.0.0
network 20.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R4
[r4]display current-configuration
[V200R003C00]
#
sysname r4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 20.200.46.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
rip 2
undo summary
version 2
network 4.0.0.0
network 20.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return