tryhackme-Investigating Windows[应急响应案例-溯源取证]
1-》Whats the version and year of the windows machine?
Windows 机器的版本和年份是什么?
方法1:查询Windows版本和年份:使用命令"winver"或"systeminfo"
Press Windows+R to open the Run prompt then type regedit then enter.
按 Windows+R 打开“运行”提示,然后键入 regedit,然后输入。
Navigate to: 导航到:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName
Answer: Windows Server 2016
答:Windows Server 2016
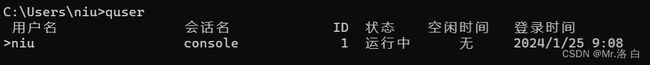
2-》Which user logged in last?
哪个用户上次登录?
方法1:使用cmd:quser 【下图只是演示】
方法2:
Navigate to: 导航到:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\LastLoggedOnUser
Answer: Administrator
答:Administrator
3-》When did John log onto the system last?
John 上次登录系统是什么时候?
Open cmd.exe and enter the following command.
打开 cmd.exe然后输入以下命令。
net user John
Answer: 03/02/2019 5:48:32 PM
答案:03/02/2019 5:48:32 PM
4-》What IP does the system connect to when it first starts?
系统首次启动时连接到哪个 IP?
Open regedit again and navigate to:
再次打开 regedit 并导航到:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\UpdateSvc
Answer: 10.34.2.3
答案:10.34.2.3
5-》What two accounts had administrative privileges (other than the Administrator user)?
哪两个帐户具有管理权限(管理员用户除外)?
方法1:
查找具有管理权限的帐户:使用命令"net localgroup administrators"。【下图只是演示】
方法2:
Open Run and enter: 打开“运行”并输入:
lusrmgr.msc
Open Groups -> Administrators
打开组 ->管理员
It is very interesting that the Guest user is part of the Administrators group.
非常有趣的是,Guest 用户是 Administrators 组的一部分。
Answer: Jenny, Guest
答:Jenny,guest
6-》Whats the name of the scheduled task that is malicous.
恶意的计划任务的名称是什么?
Open the Task Scheduler.
打开任务计划程序。
The following tasks appears to be doing something suspicious:
以下任务似乎正在执行可疑操作:
- Clean file system 清理文件系统
- Attempts to open C:\TMP\nc.ps1 -l 1348
尝试打开 C:\TMP\nc.ps1 -l 1348 - This appears to be an APT simulator
这似乎是一个 APT
- Attempts to open C:\TMP\nc.ps1 -l 1348
- GameOver
- Attempts to save LogonPasswords to a text file every 5 minutes
尝试每 5 分钟将 LogonPasswords 保存到文本文件
- Attempts to save LogonPasswords to a text file every 5 minutes
However, TryHackMe wants us to answer ‘Clean file system’.
但是,TryHackMe 希望我们回答“干净的文件系统”。
Answer: Clean file system
答:Clean file system
7-》What file was the task trying to run daily?
任务每天尝试运行什么文件?
Answer: nc.ps1
答案:nc.ps1
8-》What port did this file listen locally for?
此文件在本地侦听了哪个端口?
Answer: 1348
答案:1348
9-》When did Jenny last logon?
Jenny 上次登录是什么时候?
Open cmd.exe and type: 打开 cmd.exe并键入:
net user Jenny
Answer: Never
答:Never
10-》At what date did the compromise take place?
妥协发生在哪一天?
The ‘Clean file system’ task was created no 03/02/2019, we can assume that is the date of the compromise.
“清理文件系统”任务创建于 2019 年 3 月 2 日,我们可以假设这是入侵的日期。
Answer: 03/02/2019
答:03/02/2019
11-》At what time did Windows first assign special privileges to a new logon?
Windows 何时首次为新登录分配特殊权限?
Open Event Viewer and look for the correct entry.
打开事件查看器并查找正确的条目。
通过筛选:
可以根据:事件ID-》 事件ID1 -------- 事件ID2
可以根据:关键字-》Audit Success
可以根据:计算机名-》找jenny对应的计算机名(不是jenny)
Answer: 03/02/2019 04:04:49 PM
答案:03/02/2019 04:04:49 PM
12-》What tool was used to get Windows passwords?
使用什么工具获取 Windows 密码?
我们从前面的问题中知道,计划任务正在 C:\TMP 中执行应用程序。
打开 Windows 资源管理器并导航到:
C:\TMP\mim-out.txt
Answer: Mimikatz
答:Mimikatz
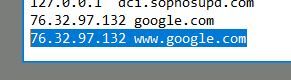
16-》Check for DNS poisoning, what site was targeted?
检查DNS中毒,针对哪个网站?
Windows hosts 文件用于将服务器或主机名映射到 IP 地址。
在 Windows 中,hosts 文件的位置是 C:\Windows\System32\drivers\etc\hosts
Answer: google.com
答:google.com
13-》What was the attackers external control and command servers IP?
攻击者的外部控制和命令服务器 IP 是什么?
根据上面的DNS解析对应的ip
C:\Windows\System32\drivers\etc\hosts.txt
Answer: 76.32.97.132
答案:76.32.97.132
14-》What was the extension name of the shell uploaded via the servers website?
通过服务器网站上传的 shell 的扩展名是什么?
Web 服务器相关的内容可能存储在 C:\inetpub\wwwroot 中。
Answer: .jsp
答案:.jsp
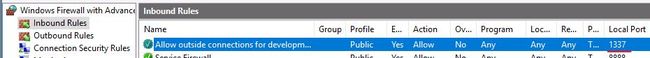
15-》What was the last port the attacker opened?
攻击者打开的最后一个端口是什么?
Open Windows Firewall and then click on Inbound Rules.
打开 Windows 防火墙,然后单击“入站规则”。
The most recent entry shows which port was opened.
最新条目显示打开了哪个端口。
Answer: 1337
答案:1337
借鉴:TryHackMe: Investigating Windows - andickinson.github.io
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第1张图片](http://img.e-com-net.com/image/info8/82945b4c129040c49e32e4b3725693c0.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第2张图片](http://img.e-com-net.com/image/info8/2183371c6abd4374acfead240e20a889.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第3张图片](http://img.e-com-net.com/image/info8/79d58a3967364b81b83919b0eab7be21.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第4张图片](http://img.e-com-net.com/image/info8/58c7b1752f4349faa4ec9d1d86eb7467.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第5张图片](http://img.e-com-net.com/image/info8/509e350b5d6244aa97fe908abb7573a6.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第6张图片](http://img.e-com-net.com/image/info8/8329c9d2619c4a1ca2c3b92990d6bf4d.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第7张图片](http://img.e-com-net.com/image/info8/4e102257c8f9409ba71de6a160956253.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第8张图片](http://img.e-com-net.com/image/info8/58201bcf9f9d4abdaca122b7ad5ddf84.jpg)
![tryhackme-Investigating Windows[应急响应案例-溯源取证]_第9张图片](http://img.e-com-net.com/image/info8/3d589adaeb984f58b6e3e8c913c5df0c.jpg)