SpringBoot整合Spring Security、jwt、mybatis前后端分离
SpringBoot整合Spring Security
- 1 前言
- 2 基本概念
-
- 2.1 单点登录
- 2.2 JWT
- 2.3 RSA
- 3 sql
- 4 认证服务器
-
- 4.1 application.yml
- 5 资源服务器
- 6
1 前言
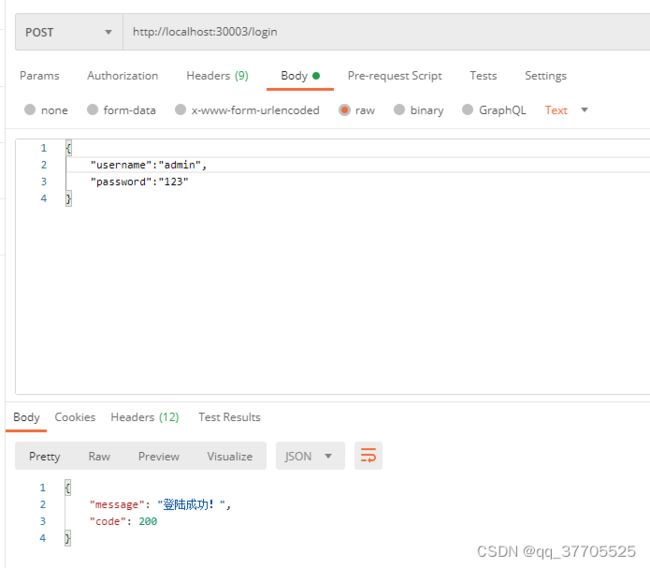
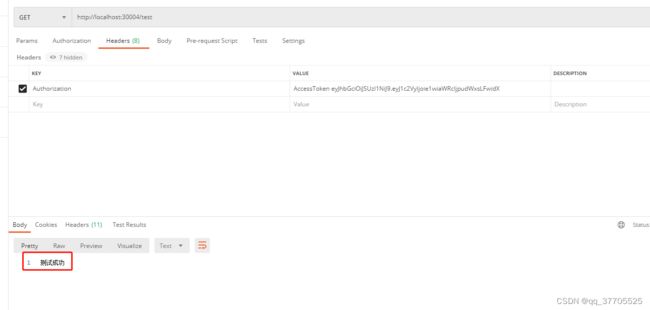
Spring Security是一个功能强大且高度可定制的身份验证和访问控制框架。提供了完善的认证机制和方法级的授权功能。是一款非常优秀的权限管理框架。它的核心是一组过滤器链,不同的功能经由不同的过滤器。这篇文章就是想通过一个小案例将Spring Security整合到SpringBoot中去。要实现的功能就是在认证服务器上登录,然后获取Token,再访问资源服务器中的资源。

2 基本概念
2.1 单点登录
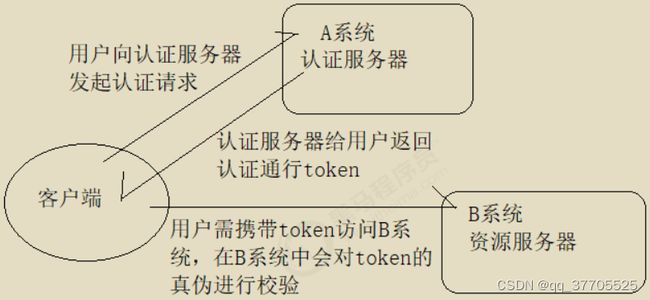
什么叫做单点登录呢。就是在一个多应用系统中,只要在其中一个系统上登录之后,不需要在其它系统上登录也可以访问其内容。举个例子,京东那么复杂的系统肯定不会是单体结构,必然是微服务架构,比如订单功能是一个系统,交易是一个系统…那么我在下订单的时候登录了,付钱难道还需要再登录一次吗,如果是这样,用户体验也太差了吧。实现的流程就是我在下单的时候系统发现我没登录就让我登录,登录完了之后系统返回给我一个Token,就类似于身份证的东西;然后我想去付钱的时候就把Token再传到交易系统中,然后交易系统验证一下Token就知道是谁了,就不需要再让我登录一次。
2.2 JWT
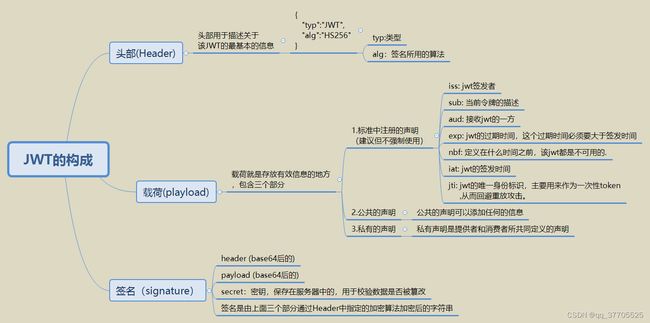
上面提到的Token就是JWT(JSON Web Token),是一种用于通信双方之间传递安全信息的简洁的、URL安全的表述性声明规范。一个JWT实际上就是一个字符串,它由三部分组成,头部、载荷与签名。为了能够直观的看到JWT的结构,我画了一张思维导图:
最终生成的JWT令牌就是下面这样,有三部分,用 . 分隔。
base64UrlEncode(JWT 头)+“.”+base64UrlEncode(载荷)+“.”+HMACSHA256(base64UrlEncode(JWT 头) + “.” + base64UrlEncode(有效载荷),密钥)
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiYWRtaW4iOnRydWV9.TJVA95OrM7E2cBab30RMHrHDcEfxjoYZgeFONFh7HgQ
2.3 RSA
从上面的例子中可以看出,JWT在加密解密的时候都用到了同一个密钥 “ robod666 ”,这将会带来一个弊端,如果被黑客知道了密钥的内容,那么他就可以去伪造Token了。所以为了安全,我们可以使用非对称加密算法RSA。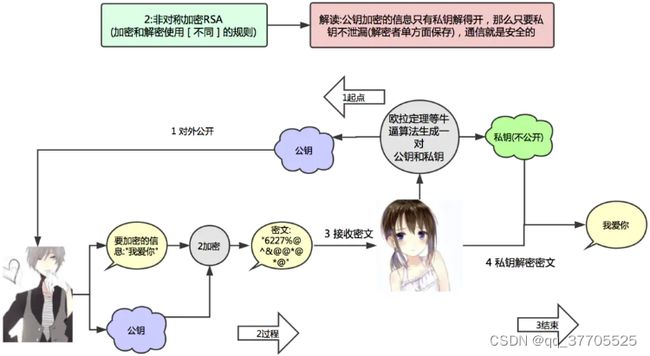
RSA的基本原理有两点:
私钥加密,持有私钥或公钥才可以解密
公钥加密,持有私钥才可解密
3 sql
-- ----------------------------
-- Table structure for sys_role
-- ----------------------------
DROP TABLE IF EXISTS `sys_role`;
CREATE TABLE `sys_role` (
`ID` int(11) NOT NULL AUTO_INCREMENT COMMENT '编号',
`ROLE_NAME` varchar(30) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL COMMENT '角色名称',
`ROLE_DESC` varchar(60) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL COMMENT '角色描述',
PRIMARY KEY (`ID`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 6 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Compact;
-- ----------------------------
-- Records of sys_role
-- ----------------------------
INSERT INTO `sys_role` VALUES (1, 'ROLE_USER', '基本角色');
INSERT INTO `sys_role` VALUES (2, 'ROLE_ADMIN', '超级管理员');
INSERT INTO `sys_role` VALUES (3, 'ROLE_PRODUCT', '管理产品');
INSERT INTO `sys_role` VALUES (4, 'ROLE_ORDER', '管理订单');
-- ----------------------------
-- Table structure for sys_user
-- ----------------------------
DROP TABLE IF EXISTS `sys_user`;
CREATE TABLE `sys_user` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(32) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL COMMENT '用户名称',
`password` varchar(120) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL COMMENT '密码',
`status` int(1) NULL DEFAULT 1 COMMENT '1开启0关闭',
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Compact;
-- ----------------------------
-- Records of sys_user
-- ----------------------------
INSERT INTO `sys_user` VALUES (1, 'xiaoming', '$2a$10$CYX9OMv0yO8wR8rE19N2fOaXDJondci5uR68k2eQJm50q8ESsDMlC', 1);
INSERT INTO `sys_user` VALUES (2, 'xiaoma', '$2a$10$CYX9OMv0yO8wR8rE19N2fOaXDJondci5uR68k2eQJm50q8ESsDMlC', 1);
-- ----------------------------
-- Table structure for sys_user_role
-- ----------------------------
DROP TABLE IF EXISTS `sys_user_role`;
CREATE TABLE `sys_user_role` (
`UID` int(11) NOT NULL COMMENT '用户编号',
`RID` int(11) NOT NULL COMMENT '角色编号',
PRIMARY KEY (`UID`, `RID`) USING BTREE,
INDEX `FK_Reference_10`(`RID`) USING BTREE,
CONSTRAINT `FK_Reference_10` FOREIGN KEY (`RID`) REFERENCES `sys_role` (`ID`) ON DELETE RESTRICT ON UPDATE RESTRICT,
CONSTRAINT `FK_Reference_9` FOREIGN KEY (`UID`) REFERENCES `sys_user` (`id`) ON DELETE RESTRICT ON UPDATE RESTRICT
) ENGINE = InnoDB CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Compact;
-- ----------------------------
-- Records of sys_user_role
-- ----------------------------
INSERT INTO `sys_user_role` VALUES (1, 1);
INSERT INTO `sys_user_role` VALUES (2, 1);
INSERT INTO `sys_user_role` VALUES (1, 3);
INSERT INTO `sys_user_role` VALUES (2, 4);
SET FOREIGN_KEY_CHECKS = 1;
4 认证服务器
4.1 application.yml
server:
port: 30003
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql://localhost:3306/security3?useSSL=false&serverTimezone=GMT%2B8&useUnicode=true&characterEncoding=utf-8
username: root
password: root
thymeleaf:
cache: false
check-template: true
check-template-location: true
servlet:
content-type: text/html
enabled: true
encoding: UTF-8
excluded-view-names:
mode: HTML
prefix: classpath:/templates/
suffix: .html
mvc:
static-path-pattern: /static/**
web:
resources:
static-locations: classpath:/static
mybatis:
configuration:
map-underscore-to-camel-case: true
log-impl: org.apache.ibatis.logging.stdout.StdOutImpl
mapper-locations: classpath:mapper/*.xml
type-aliases-package: org.example.security.model
logging:
level:
org:
springframework:
security: debug
rsa:
key:
pubKeyPath: D:\temp\id_key_rsa.pub
priKeyPath: D:\temp\id_key_rsa
RsaKeyProperties
@Data
@ConfigurationProperties("rsa.key") //指定配置文件的key
public class RsaKeyProperties {
private String pubKeyPath;
private String priKeyPath;
private PublicKey publicKey;
private PrivateKey privateKey;
@PostConstruct
public void createKey() throws Exception {
this.publicKey = RsaUtils.getPublicKey(pubKeyPath);
this.privateKey = RsaUtils.getPrivateKey(priKeyPath);
}
}
WebSecurityConfig
@Configuration
@EnableWebSecurity //加了这个注解才能写SpringSecurity相关的配置
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
private final UserService userService;
private final RsaKeyProperties rsaKeyProperties;
public WebSecurityConfig(UserService userService, RsaKeyProperties rsaKeyProperties) {
this.userService = userService;
this.rsaKeyProperties = rsaKeyProperties;
}
@Bean
public BCryptPasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
/**
* 认证用户的来源
*
* @param auth
* @throws Exception
*/
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
//数据库中
auth.userDetailsService(userService).passwordEncoder(passwordEncoder());
}
/**
* 配置SpringSecurity相关信息
*
* @param http
* @throws Exception
*/
@Override
public void configure(HttpSecurity http) throws Exception {
http.csrf().disable() //关闭csrf
.addFilter(new JwtLoginFilter(super.authenticationManager(),rsaKeyProperties))
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS); //禁用session
}
}
@Data
public class Payload {
private String id;
private T userInfo;
private Date expiration;
}
JwtLoginFilter
public class JwtLoginFilter extends UsernamePasswordAuthenticationFilter {
private AuthenticationManager authenticationManager;
private RsaKeyProperties rsaKeyProperties;
public JwtLoginFilter(AuthenticationManager authenticationManager, RsaKeyProperties rsaKeyProperties) {
this.authenticationManager = authenticationManager;
this.rsaKeyProperties = rsaKeyProperties;
}
/**
* 这个方法是用来去尝试验证用户的,父类中是从POST请求的form表单中获取,但是这里不是,所以需要重写
* @param request
* @param response
* @return
* @throws AuthenticationException
*/
@Override
public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException {
try {
SysUser user = JSONObject.parseObject(request.getInputStream(),SysUser.class);
return authenticationManager.authenticate(
new UsernamePasswordAuthenticationToken(
user.getUsername(),
user.getPassword())
);
} catch (Exception e) {
try {
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_UNAUTHORIZED);
PrintWriter out = response.getWriter();
Map map = new HashMap<>();
map.put("code", HttpServletResponse.SC_UNAUTHORIZED);
map.put("message", "账号或密码错误!");
out.write(new ObjectMapper().writeValueAsString(map));
out.flush();
out.close();
} catch (Exception e1) {
e1.printStackTrace();
}
throw new RuntimeException(e);
}
}
/**
* 成功之后执行的方法,父类中是放入session,不符合我们的要求,所以重写
* @param request
* @param response
* @param chain
* @param authResult
* @throws IOException
* @throws ServletException
*/
@Override
public void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException {
SysUser sysUser = new SysUser();
sysUser.setUsername(authResult.getName());
sysUser.setRoles((List) authResult.getAuthorities());
String token = JwtUtils.generateTokenExpireInMinutes(sysUser,rsaKeyProperties.getPrivateKey(),24*60);
response.addHeader("Authorization", "RobodToken " + token);
try {
//登录成功时,返回json格式进行提示
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_OK);
PrintWriter out = response.getWriter();
Map map = new HashMap(4);
map.put("code", HttpServletResponse.SC_OK);
map.put("message", "登陆成功!");
out.write(new ObjectMapper().writeValueAsString(map));
out.flush();
out.close();
} catch (Exception e1) {
e1.printStackTrace();
}
}
}
public interface UserService extends UserDetailsService {
}
@Service("userService")
public class UserServiceImpl implements UserService {
private final UserMapper userMapper;
public UserServiceImpl(UserMapper userMapper) {
this.userMapper = userMapper;
}
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
SysUser sysUser = userMapper.findByUsername(username);
return sysUser;
}
}
@SpringBootApplication
@MapperScan("com.example.security3.mapper")
@EnableConfigurationProperties(RsaKeyProperties.class) //将配置类放入Spring容器中
public class Security3Application {
public static void main(String[] args) {
SpringApplication.run(Security3Application.class,args);
}
}
5 资源服务器
server:
port: 30004
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql:///security3?useUnicode=true&characterEncoding=UTF-8&serverTimezone=UTC
username: root
password: root
mybatis:
type-aliases-package: com.example.resource.entity
configuration:
map-underscore-to-camel-case: true
logging:
level:
com: debug
rsa:
key:
pubKeyPath: D:\temp\id_key_rsa.pub
public class JwtVerifyFilter extends BasicAuthenticationFilter {
private RsaKeyProperties rsaKeyProperties;
public JwtVerifyFilter(AuthenticationManager authenticationManager, RsaKeyProperties rsaKeyProperties) {
super(authenticationManager);
this.rsaKeyProperties = rsaKeyProperties;
}
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain chain)
throws IOException, ServletException {
String header = request.getHeader("Authorization");
//没有登录
if (header == null || !header.startsWith("RobodToken ")) {
chain.doFilter(request, response);
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_FORBIDDEN);
PrintWriter out = response.getWriter();
Map map = new HashMap(4);
map.put("code", HttpServletResponse.SC_FORBIDDEN);
map.put("message", "请登录!");
out.write(new ObjectMapper().writeValueAsString(map));
out.flush();
out.close();
return;
}
//登录之后从token中获取用户信息
String token = header.replace("RobodToken ","");
SysUser sysUser = JwtUtils.getInfoFromToken(token, rsaKeyProperties.getPublicKey(), SysUser.class).getUserInfo();
if (sysUser != null) {
Authentication authResult = new UsernamePasswordAuthenticationToken
(sysUser.getUsername(),null,sysUser.getAuthorities());
SecurityContextHolder.getContext().setAuthentication(authResult);
chain.doFilter(request, response);
}
}
}
@Data
@Component
@ConfigurationProperties("rsa.key") //指定配置文件的key
public class RsaKeyProperties {
private String pubKeyPath;
private PublicKey publicKey;
@PostConstruct
public void createKey() throws Exception {
this.publicKey = RsaUtils.getPublicKey(pubKeyPath);
}
}
@Configuration
@EnableWebSecurity //加了这个注解才能写SpringSecurity相关的配置
@EnableGlobalMethodSecurity(securedEnabled = true) //开启权限控制的注解支持,securedEnabled表示SpringSecurity内部的权限控制注解开关
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
private final RsaKeyProperties rsaKeyProperties;
public WebSecurityConfig(RsaKeyProperties rsaKeyProperties) {
this.rsaKeyProperties = rsaKeyProperties;
}
/**
* 配置SpringSecurity相关信息
*
* @param http
* @throws Exception
*/
@Override
public void configure(HttpSecurity http) throws Exception {
http.csrf().disable() //关闭csrf
.authorizeRequests()
.antMatchers("/**").hasAnyRole("USER") //角色信息
.anyRequest() //其它资源
.authenticated() //表示其它资源认证通过后
.and()
.addFilter(new JwtVerifyFilter(super.authenticationManager(),rsaKeyProperties))
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS); //禁用session
}
}
@Data
public class Payload {
private String id;
private T userInfo;
private Date expiration;
}
@RestController
@RequestMapping("/product")
public class ProductController {
@Secured("ROLE_USER")
@RequestMapping("/findAll")
public String findAll() {
return "测试";
}
}
6
封装权限信息的类实现GrantedAuthority接口,并实现里面的getAuthority()方法
实现自己的Token校验过滤器继承自BasicAuthenticationFilter,并重写doFilterInternal()方法,实现自己的业务逻辑
编写Spring Security的配置类继承WebSecurityConfigurerAdapter,重写configure()方法添加自定义的过滤器,并添加@EnableGlobalMethodSecurity(securedEnabled = true)注解开启注解权限控制的功能
如果使用RSA非对称加密,就准备好RSA的配置类,然后在启动类中加入注解将其加入IOC容器中,注意这里不要只要配置公钥即可
总结
SpringBoot 整合 Spring Security到这里就结束了。文章只是简单的说了一下整合的流程,很多其它的东西都没有说,比如各个过滤器都有什么作用等。还有,这里采用的认证服务器和资源服务器分离的方式,要是集成在一起也是可以的。