linux防火墙实战
firewall-cmd --reload
firewall-cmd --list-all-zones 查看所有区域信息
firewall-cmd --list-all --zone=external
firewall-cmd --get-active-zones 查看活跃区域
firewall-cmd --zone=dmz --list-ports 查看*区域内开启的接口
firewall-cmd --permanent --zone=external --add-interface=eth1 在*区域内添加接口
firewall-cmd --zone=external --add-port=12345/tcp --permanent 在*区域添加接口
firewall-cmd --zone=dmz --add-service=https --permanent 在*区域添加服务
firewall-cmd --zone=dmz --add-port=12345/tcp --permanent 在*区域添加端口
firewall-cmd --zone=dmz --remove-service=http --permanent 在*区域移除服务
firewall-cmd --zone=dmz --remove-port=12345/tcp --permanent 在*区域移除端口
firewall-cmd --zone=dmz --add-icmp-block=echo-request --permanent
firewall-cmd --zone=dmz --list-icmp-blocks
firewall-cmd --zone=dmz --add-icmp-block=echo-reply --permanent
firewall-cmd --zone=external --add-rich-rule=‘rule family=ipv4 source address=192.168.254.0/24 masquerade’ --permanent 启用伪装
firewall-cmd --zone=external --add-forward-port=port=443:proto=tcp:to addr=192.168.16.22 --permanent 端口转换
yum -y install httpd mod_ssl
echo “
www.gsy.com
” > /var/www/html/index.html
防火墙和核心防护默认关闭
echo “net.ipv4.ip_forward=1” >> /etc/sysctl.conf
sysctl -p
[root@ct ~]# hostnamectl set-hostname gate
[root@ct ~]# su
[root@gate network-scripts]# ip addr
2: eth0: mtu 1500 qdisc pfifo_fast
inet 192.168.254.20/24 brd 192.168.254.255 scope global eth0
3: eth1: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
inet 192.168.247.20/24 brd 192.168.247.255 scope global eth1
4: eth2: mtu 1500 qdisc pfifo_fast
inet 192.168.16.20/24 brd 192.168.16.255 scope global eth2
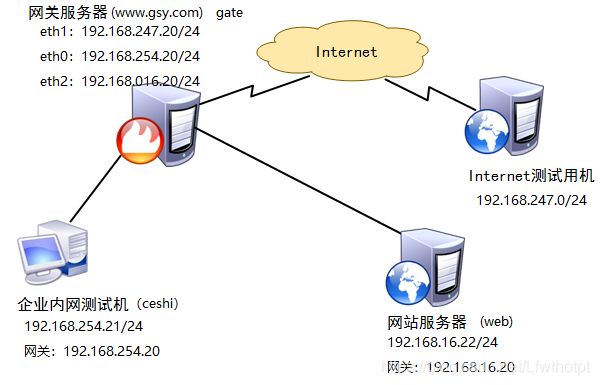
gate 网关服务器(www.gsy.com)
eth1:192.168.247.20 nat
eth0:192.168.254.20 vm1
eth2:192.168.16.20 vm2
网站服务器(web):192.168.16.22
网关:192.168.16.20
[root@comp2 ~]# hostnamectl set-hostname web
[root@comp2 ~]# su
[root@web ~]# ip addr
3: eth1: mtu 1500 qdisc pfifo_fast
inet 192.168.16.22/24 brd 192.168.16.255 scope global eth1
企业内网测试机(ceshi):192.168.254.21
[root@ceshi ~]# ip addr
2: eth0: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
inet 192.168.254.21/24 brd 192.168.254.255 scope global eth0
需求描述
1
网关服务器连接互联网网卡eth1地址为192.168.247.20,为公网IP地址,分配到firewall的external区域;连接内网网卡eth0地址为192.168.254.20,分配到firewall的trusted区域;连接服务器网卡eth2地址为192.168.16.20,分配到firewall的dmz区域
–permanent参数 : 携带该参数表示永久配置,否则表示运行时配置
[root@gate ssh]# echo "net.ipv4.ip_forward=1" >> /etc/sysctl.conf
You have new mail in /var/spool/mail/root
[root@gate ssh]# sysctl -p
net.ipv4.ip_forward = 1
[root@gate ssh]# systemctl restart network
[root@gate network-scripts]# firewall-cmd --get-active-zones
FirewallD is not running
You have new mail in /var/spool/mail/root
[root@gate network-scripts]# systemctl start firewalld
[root@gate network-scripts]# systemctl enable firewalld
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
[root@gate network-scripts]# firewall-cmd --get-active-zones
[root@gate network-scripts]#
[root@gate network-scripts]# firewall-cmd --permanent --zone=external --add-interface=eth1
success
[root@gate ssh]# firewall-cmd --reload
[root@gate ssh]# systemctl restart firewalld
You have new mail in /var/spool/mail/root
[root@gate network-scripts]# firewall-cmd --get-active-zones
external
interfaces: eth1
[root@gate network-scripts]# firewall-cmd --zone=trusted --add-interface=eth0 --permanent
success
[root@gate ssh]# firewall-cmd --reload
success
[root@gate network-scripts]# firewall-cmd --get-active-zones
external
interfaces: eth1
trusted
interfaces: eth0
[root@gate network-scripts]# firewall-cmd --zone=dmz --add-interface=eth2 --permanent
success
[root@gate ssh]# firewall-cmd --reload
[root@gate network-scripts]# firewall-cmd --get-active-zones
dmz
interfaces: eth2
external
interfaces: eth1
trusted
interfaces: eth0
2
网站服务器和网关服务器均通过SSH来远程管理,为了安全,将SSH默认端口改为12345
[root@gate network-scripts]# cd /etc/ssh
[root@gate ssh]# ls
moduli sshd_config ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub
ssh_config ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key
[root@gate ssh]# vi sshd_config
17 Port 12345
19 ListenAddress 0.0.0.0
[root@gate ssh]# systemctl restart sshd
[root@gate ssh]# yum install net-tools -y
[root@gate ssh]# netstat -natp | grep 12345
tcp 0 0 0.0.0.0:12345 0.0.0.0:* LISTEN 108697/sshd
tcp6 0 0 :::12345 :::* LISTEN 108697/sshd
[root@web ~]# vim /etc/ssh/sshd_config
17 Port 12345
19 ListenAddress 0.0.0.0
[root@web ~]# systemctl restart sshd
[root@web ~]# netstat -natp | grep 12345
tcp 0 0 0.0.0.0:12345 0.0.0.0:* LISTEN 105032/sshd
tcp6 0 0 :::12345 :::* LISTEN 105032/sshd
[root@gate ssh]# ssh -p 12345 [email protected]
Last login: Fri Apr 10 04:24:17 2020 from 192.168.16.20
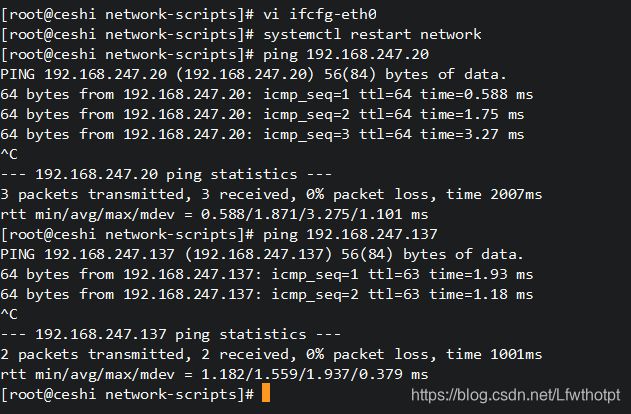
[root@web ~]# vi ifcfg-eth0
[root@web ~]# ssh -p 12345 [email protected]
ssh: connect to host 192.168.16.20 port 12345: No route to host
[root@gate ssh]# firewall-cmd --zone=dmz --list-ports
[root@gate ssh]# firewall-cmd --zone=external --list-ports
[root@gate ssh]# firewall-cmd --zone=external --add-port=12345/tcp --permanent
success
[root@gate ssh]# firewall-cmd --zone=dmz --add-port=12345/tcp --permanent
success
[root@gate ssh]# firewall-cmd --zone=trusted --add-port=12345/tcp --permanent
[root@gate ssh]# firewall-cmd --reload
[root@gate ssh]# firewall-cmd --zone=dmz --list-ports
12345/tcp
[root@gate ssh]# firewall-cmd --zone=external --list-ports
12345/tcp
[root@gate ssh]# vim ssh_config
41 Port 12345
[root@web ~]# ssh -p 12345 [email protected]
Last login: Thu Apr 9 20:25:28 2020 from 192.168.16.22
[root@gate ~]#
3
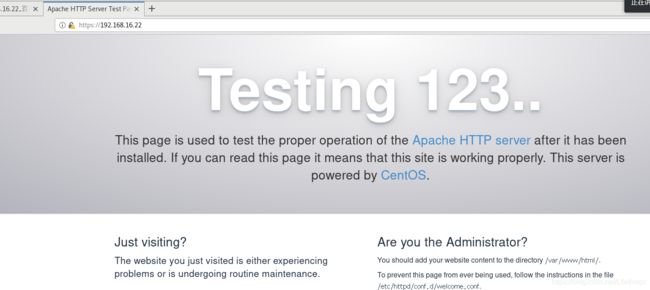
网站服务器开启HTTPS,过滤未加密的HTTP流量
[root@web ~]# yum -y install httpd mod_ssl
[root@web ~]# systemctl start httpd
You have new mail in /var/spool/mail/root
[root@web ~]# systemctl enable httpd
Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service.
[root@web ~]# echo "www.gsy.com" > /var/www/html/index.html
[root@web ~]# systemctl status firewalld
Active: inactive (dead)
[root@web ~]# systemctl start firewalld
[root@web ~]# systemctl enable firewalld
[root@web ~]# firewall-cmd --zone=dmz --add-interface=eth1 --permanent
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --zone=dmz --add-service=https --permanent
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --zone=dmz --remove-service=http --permanent
Warning: NOT_ENABLED: 'http' not in 'dmz'
success
[root@web ~]#
[root@web ~]# firewall-cmd --zone=dmz --list-services
https ssh
[root@web ~]# firewall-cmd --zone=dmz --list-ports
[root@web ssh]# firewall-cmd --zone=dmz --add-port=12345/tcp --permanent
success
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --list-all-zones
dmz (active)
target: default
icmp-block-inversion: no
interfaces: eth1
services: https ssh
ports: 12345/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
[root@web ~]# firewall-cmd --zone=dmz --add-port=443/tcp --permanent
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --zone=dmz --list-ports
12345/tcp 443/tcp
4
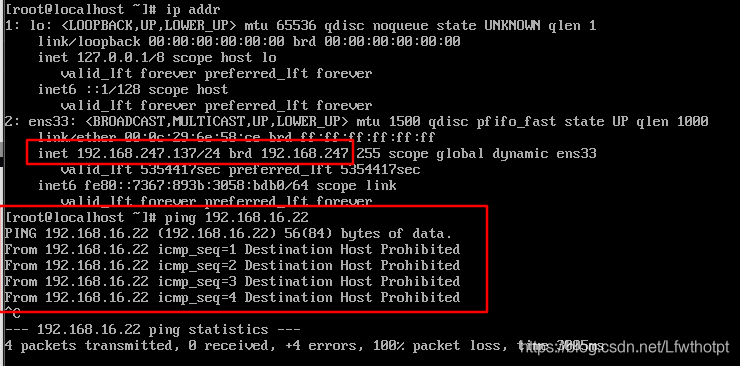
网站务器拒绝ping,网关服务器拒绝来自互联网上的ping
[root@web ~]# firewall-cmd --get-active-zones
dmz
interfaces: eth1
[root@web ~]# firewall-cmd --zone=dmz --list-icmp-blocks
[root@web ~]# firewall-cmd --zone=dmz --add-icmp-block=echo-request --permanent
You have mail in /var/spool/mail/root
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --zone=dmz --list-icmp-blocks
echo-request
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-ZV27i6LR-1586519015939)(G:\GSY\Documents\typora图片\1586444573508.png)]
[root@web ~]# firewall-cmd --zone=dmz --add-icmp-block=echo-reply --permanent
[root@web ~]# firewall-cmd --reload
[root@web ~]# firewall-cmd --zone=dmz --list-icmp-blocks
echo-request echo-reply
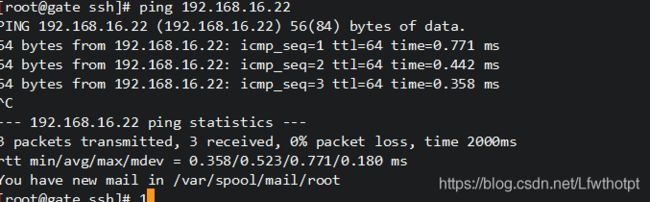
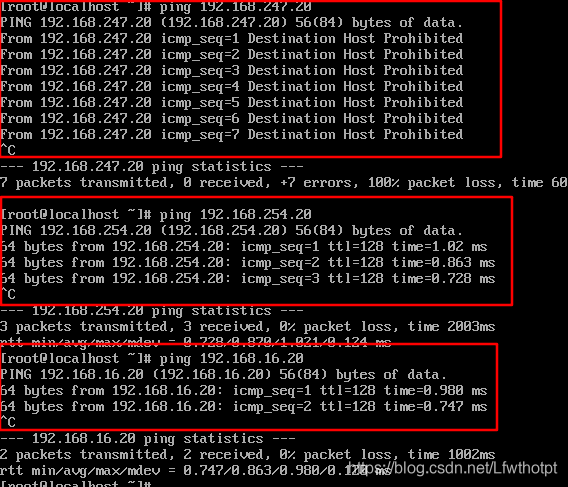
公网192.168.247.0网段的主机ping失败
网关服务器拒绝来自互联网上的ping
[root@gate ssh]# firewall-cmd --zone=external --list-icmp-block
[root@gate ssh]# firewall-cmd --zone=external --add-icmp-block=echo-request --permanent
success
[root@gate ssh]# firewall-cmd --reload
[root@gate ssh]# firewall-cmd --zone=external --list-icmp-block
echo-request
[root@gate ssh]# firewall-cmd --zone=external --add-icmp-block=echo-reply --permanent
[root@gate ssh]# firewall-cmd --reload
success
5
公司内网用户需要通过网关服务器共享上网
[root@kibana ~]# yum install httpd -y
[root@kibana ~]# systemctl start httpd
[root@kibana ~]# systemctl enable httpd
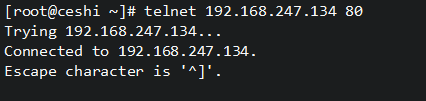
[root@gate ~]# yum install telnet -y
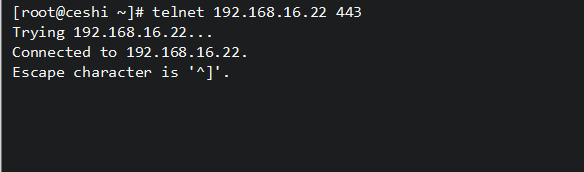
[root@gate ~]# telnet 192.168.247.134 80
Trying 192.168.247.134...
Connected to 192.168.247.134.
Escape character is '^]'.
在网关服务器上查看是否开启伪装
[root@gate ~]# firewall-cmd --list-all --zone=external
external (active)
target: default
icmp-block-inversion: no
interfaces: eth1
sources:
services: ssh
ports: 12345/tcp
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks: echo-request
rich rules:
命令启动伪装 192.168.254.0/24
[root@gate ~]# firewall-cmd --zone=external --add-rich-rule='rule family=ipv4 source address=192.168.254.0/24 masquerade' --permanent
success
[root@gate ~]# firewall-cmd --reload
[root@gate ~]# firewall-cmd --list-all --zone=external
external (active)
target: default
icmp-block-inversion: no
interfaces: eth1
sources:
services: ssh
ports: 12345/tcp
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks: echo-request
rich rules:
rule family="ipv4" source address="192.168.254.0/24" masquerade
[root@gate ssh]# echo "net.ipv4.ip_forward=1" >> /etc/sysctl.conf
You have new mail in /var/spool/mail/root
[root@gate ssh]# sysctl -p
net.ipv4.ip_forward = 1
[root@gate ssh]# systemctl restart network
指定网关,
6
互联网用户需要访问网站服务器
[root@gate ~]# firewall-cmd --zone=external --add-forward-port=port=443:proto=tcp:to addr=192.168.16.22 --permanent
success
放通443端口
[root@gate ~]# firewall-cmd --reload
success
firewalld支持两种类型的网络地址转换
- ip地址伪装(masquerade)
- 可以实现局域网多个地址共享单一公网地址上网
- ip地址伪装仅支持IPv4
- 默认external区域启用伪装
- 端口转发(forward-port)
- 也成为目的地址转换或端口映射
- 通过端口转发,指定IP地址及端口的流量将被转发到相同计算机上的不同端口;或者转发到不同计算机上的端口
地址伪装配置
- 为指定区域增加地址伪装功能
firewall-cmd --permanent --zone=dmz --add-masquerade --timeout=86400
–timeout=86400,在86400秒后自动删除该功能 - 为指定区域删除地址伪装功能
firewall-cmd --permanent --zone=dmz --remove-masquerade - 查询指定区域是否开启地址伪装功能
firewall-cmd --permanent --zone=dmz --query-masquerade
端口转发配置
- 列出端口转发配置
firewall-cmd --permanent --zone=external --list-forward-ports - 添加端口转发规则
firewall-cmd --permanent --zone=external --add-forward-port=port=portid[-portid]:proto=protocol[:toport=portid[-portid]][:toaddr=address[/mask]][–timeout=seconds] - 删除端口转发规则
firewall-cmd --permanent --zone=external --remove-forward-port=port=portid[-portid]:proto=protocol[:toport=portid[-portid]][:toaddr=address[/mask]] - 查询端口转发规则
firewall-cmd --permanent --zone=external --query-forward-port=port=portid[-portid]:proto=protocol[:toport=portid[-portid]][:toaddr=address[/mask]]
firewalld直接规则
- 直接规则(direct interface)
允许管理员手动编写的iptables、ip6tables和ebtables规则插入到firewalld管理的区域中
通过firewall-cmd命令中的–direct选项实现
除显示插入方式之外,优先匹配直接规则 - 自定义规则链
firewalld自动为配置了规则的区域创建自定义规则链
IN_区域名_deny:存放拒绝语句,优先于"IN_区域名_allow"的规则
IN_区域_allow:存放允许语句
问题排障方法
1.出现问题:A服务器链接B服务器,链接某个功能模块连接不上
2.解决思路:
检查B服务器的功能模块有没有开启
检查环境
检查配置文件
重启服务、或者重载服务
本地验证ssh -p 端口号 ip地址(回环口、接口IP)
检查B服务器的防火墙
检查接口配置信息,查看功能服务是否正常
检查A服务器的防火墙
检查接口配置信息
telnet IP地址 端口