js解密——携程景点
js解密——携程景点
摘要:无意中发现携程首页游记js加密还是挺简单的,就是通过断点获取一系列固定值和获取当前时间戳。
页面分析
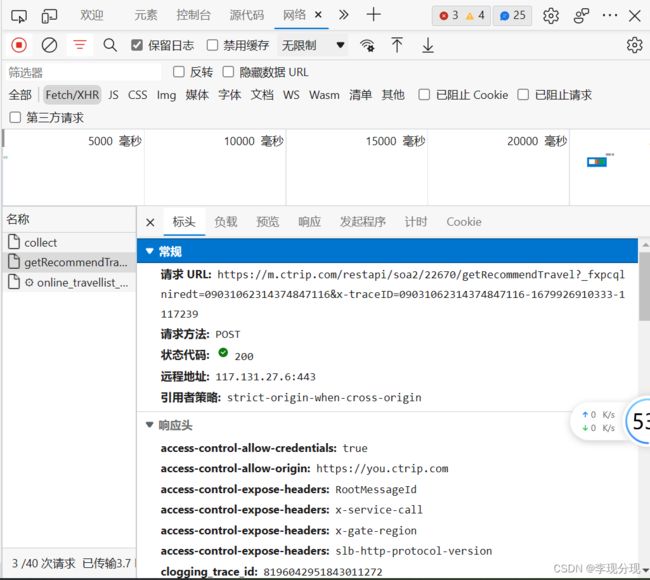
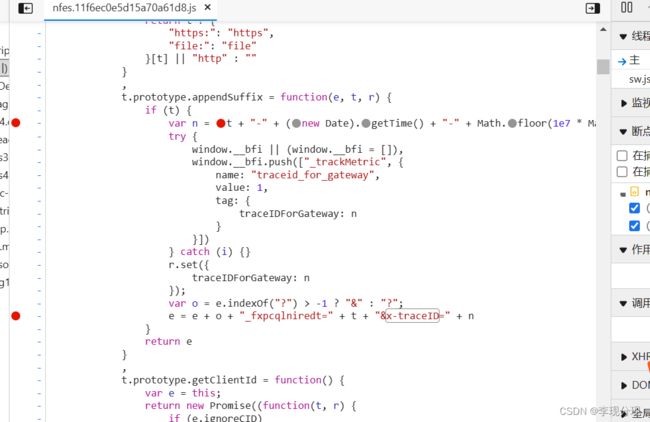
x-traceID是关键,需要查看源码断点得出
x-traceID: 09031062314374847116-1679926910333-1117239
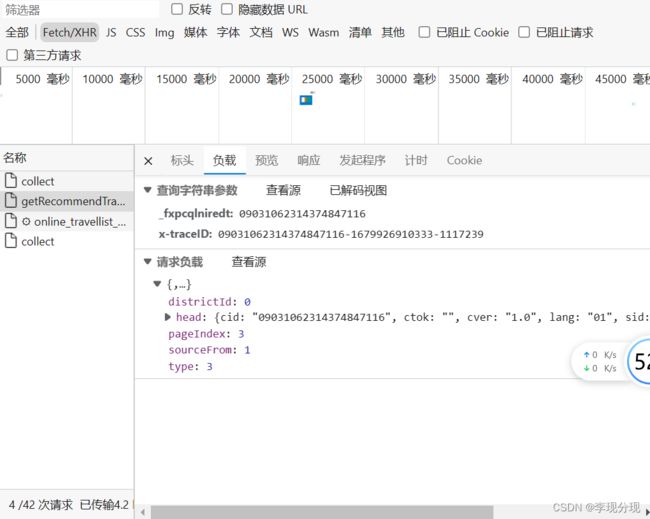
还有携带json数据,pageIndex是页码,for循环改变pageIndex值
data = {
"head": {
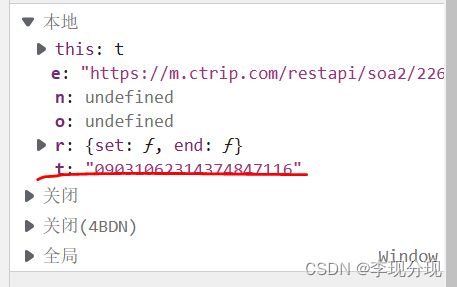
"cid": "09031062314374847116",
"ctok": "", "cver": "1.0", "lang": "01", "sid": "8888",
"syscode": "999",
"auth": "",
"xsid": "",
"extension": []
},
"districtId": 0,
"sourceFrom": 1,
"type": 3,
"pageIndex": 1}
断点分析
- 点击查看源码
- ctrl+F快速定位x-traceID,并如图打上断点
e = e + o + "_fxpcqlniredt=" + t + "&x-traceID=" + n
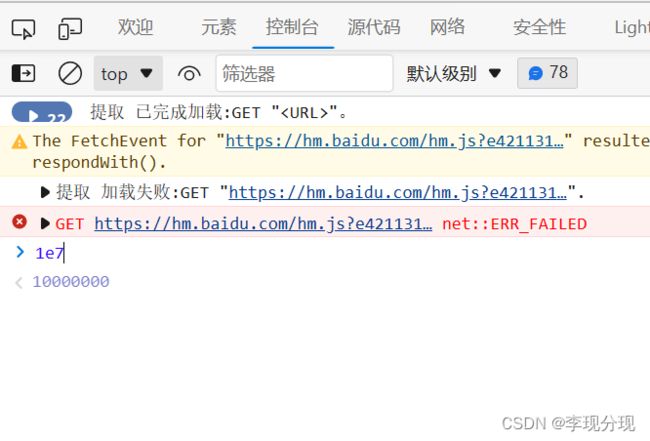
t是固定值,1e7也是,如下图得出
var n = t + "-" + (new Date).getTime() + "-" + Math.floor(1e7 * Math.random());
参数都获得,就需要python代码实现解析了
代码编写
以下代码得出x-traceID的值
import random
import time
t="09031062314374847116"
time=round(time.time()*1000)
num=int(10000000*random.random())
n=t+"-"+str(time)+"-"+str(num)
print(n)
#输出结果:09031062314374847116-1680004916269-3199960
请求
源码:
import random
import requests
import time
t="09031062314374847116"
time=round(time.time()*1000)
num=int(10000000*random.random())
n=t+"-"+str(time)+"-"+str(num)
print(n)
headers={
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36 Edg/111.0.1661.41',
'referer': 'https://you.ctrip.com/',
}
for i in range(1,3):
data = {
"head": {
"cid": "09031062314374847116",
"ctok": "", "cver": "1.0", "lang": "01", "sid": "8888",
"syscode": "999",
"auth": "",
"xsid": "",
"extension": []
},
"districtId": 0,
"sourceFrom": 1,
"type": 3,
"pageIndex": i}
url='https://m.ctrip.com/restapi/soa2/22670/getRecommendTravel?_fxpcqlniredt=09031062314374847116&x-traceID='+str(n)
res=requests.post(url,headers=headers,json=data)
print(res)
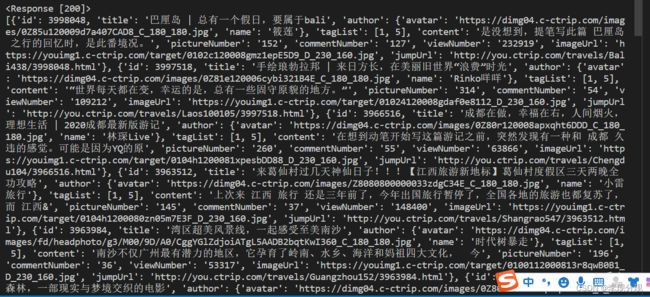
print(res.json()['travelInfoList'])
print('-----------------')