visual studio 2019 详细步骤实现DLL注入
一、创建新项目——动态链接库
#include "pch.h"
#include"windows.h"
#include"tchar.h"
#pragma comment(lib,"urlmon.lib")
HMODULE g_hMod = NULL;
DWORD WINAPI ThreadProc(LPVOID lParam)
{
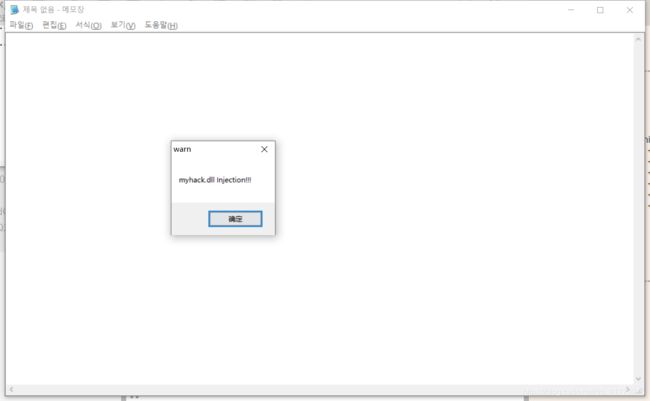
MessageBox(NULL, TEXT("myhack.dll Injection!!!"), TEXT("warn"), 0);
return 0;
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
HANDLE hThread = NULL;
g_hMod = (HMODULE)hModule;
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
OutputDebugString(L"myhack.dll Injection!!!");
hThread = CreateThread(NULL, 0, ThreadProc, NULL, 0, NULL);
CloseHandle(hThread);
break;
}
return TRUE;
}
生成——生成解决方案
找到路径内的Dll2.dll
二、创建新项目——控制台应用
源代码:
#include生成——生成解决方案
将上一步生成的dll文件放入此文件夹
我把exe重命名为Inject.exe
dll重命名为myhack.exe
打开notepad.exe
下载链接:https://pan.baidu.com/s/1_ZFI4niw1rYRU_yvT2cUdA
提取码:tq41
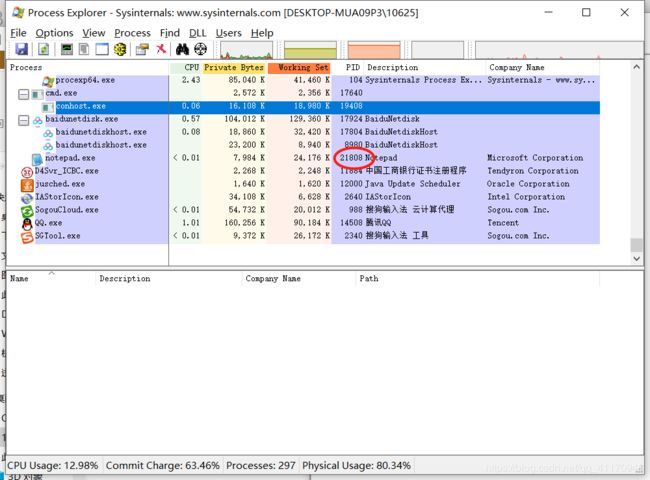
打开process explorer
链接:https://pan.baidu.com/s/1OOTde_GjICum92wF4ktPug
提取码:1fhr
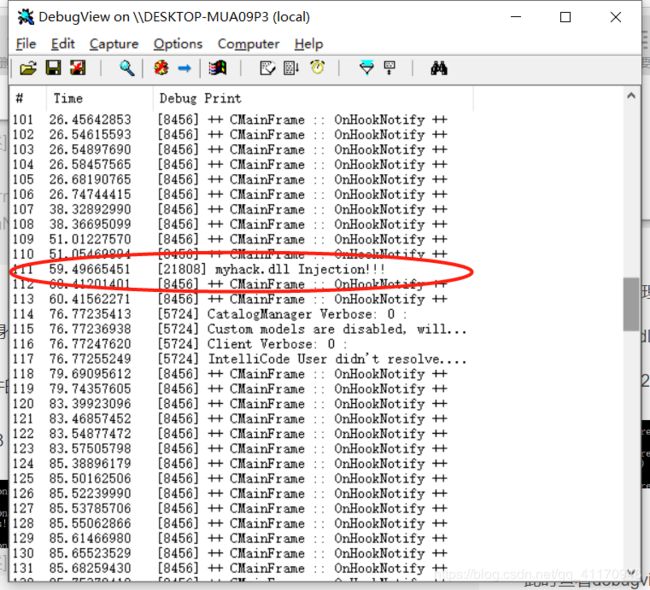
打开debugview
链接:https://pan.baidu.com/s/11gbzZrdYqO5LBgOojaDYHQ
提取码:x6g1
打开cmd,以管理员身份运行
cd到存放exe和dll文件的目录
输入 Inject.exe 20808 myhack.dll
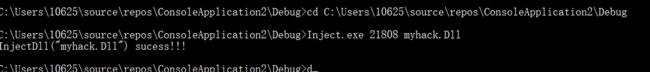
输出如上图
再查看notepad
再查看process explorer
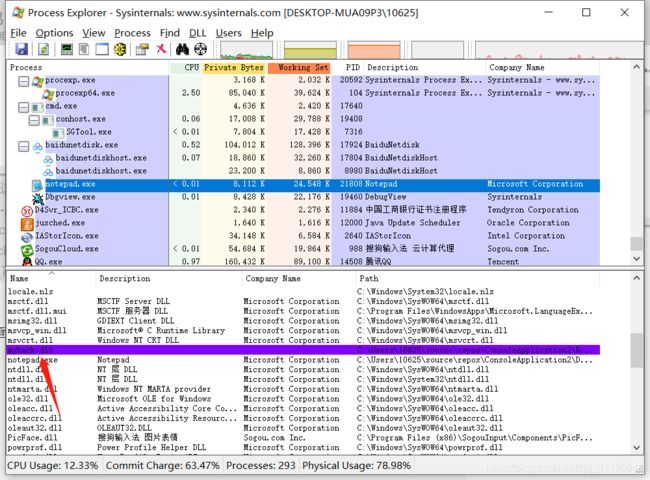
表示myhack.dll注入成功
参考书籍《逆向工程核心原理》